Kabbalah System Theory
Foundations of a postmodern cybernetics
The most consequential infrastructure now being built is not visible in skylines or satellite images. It lives in ledgers, indicators, identity schemes, conditional payment rails, and emergency protocols: a control stack that can bind global policy targets to individual transactions in real time. Its components are openly documented, framed as efficiency, inclusion, resilience, ‘better data’, ‘faster response’.
What is missing is a language precise enough to describe the architecture as a whole.
Abstract
This paper reconstructs Kabbalah System Theory (KST), as developed by Burstein and Negoita (2011–2016), as a rigorous analytical framework for modern hierarchical control and programmable governance. It first restates KST in operational terms: a three-level, ten-position control architecture (ChaBaD / ChaGaT / NHY) organised by information frequency into standards and registries, monitoring and evaluation, and execution and settlement, with Da’at as internal model and Yesod as actuation layer. It then formalises a recursive holarchic algorithm in which each ‘holon’ (from international bodies to individual transactions) runs the same control loop, linked vertically by outbound commands (Netzach → Keter) and inbound outcomes (Malkuth → Hod). Using this lens, the paper maps historical and contemporary infrastructures — PPBS, Results-Based Management, the UN SDG system, and especially the BIS Innovation Hub’s unified-ledger/CBDC and tokenisation projects — and shows that, taken together, they progressively realise a structurally complete KST-style architecture: from macro-level planning and indicators to micro-level, point-of-use enforcement via digital identity, conditional access, and programmable money.
The analysis then introduces the qliphothic ‘emergency’ inversion of the same architecture, in which opaque models, expanded surveillance, automated gating, and underspecified ‘complex shock’ mechanisms (e.g. the proposed UN Emergency Platform) enable a state of exception to be instantiated as durable infrastructure rather than temporary deviation. The paper argues that this convergence does not require conspiracy or esoteric intent: KST captures a recurring control grammar that complex institutions independently rediscover. This grammar is normatively ambivalent. It can support accountable, evidence-based governance; it can also implement computational conditional sovereignty, infrastructural coercion, and permanent emergency.
The concluding section sketches eight structural interventions — around transparency, plurality, subsidiarity, execution rails, and emergency sunset constraints — as concrete design levers for bending an already-emerging KST architecture toward contestability rather than closure.
1. Introduction to Kabbalah System Theory
Between 2011 and 2016, Gabriel Burstein and Constantin Virgil Negoiță published a series of peer-reviewed papers developing what they termed ‘Kabbalah System Theory’ (KST) — a framework for analysing complex hierarchical control systems. Published in venues including Kybernetes, Systems, Applied Mathematics, and International Journal of Advanced Research in Artificial Intelligence, these papers reinterpreted the Kabbalistic Tree of Life not as mystical symbolism but as a ready-made ten-node control topology with precise structural properties.
They explicitly model the Tree of Life as a hierarchical three-level feedback system for ‘humanistic systems’ — systems involving human decision-making, knowledge, emotions, and behaviour. The papers made specific structural claims formulated using category theory, control engineering principles, cybernetics, and general systems theory. The framework describes feedback loops, internal model principles, pullback and pushout operations for aggregation and system coupling, and most critically, a fractal recursive structure where each component contains the complete pattern at a smaller scale.
The timing matters: these papers were published between 2011 and 2016, establishing a complete theoretical framework years before the infrastructure we will examine was designed.
1.1. The Three-Level Hierarchical Structure
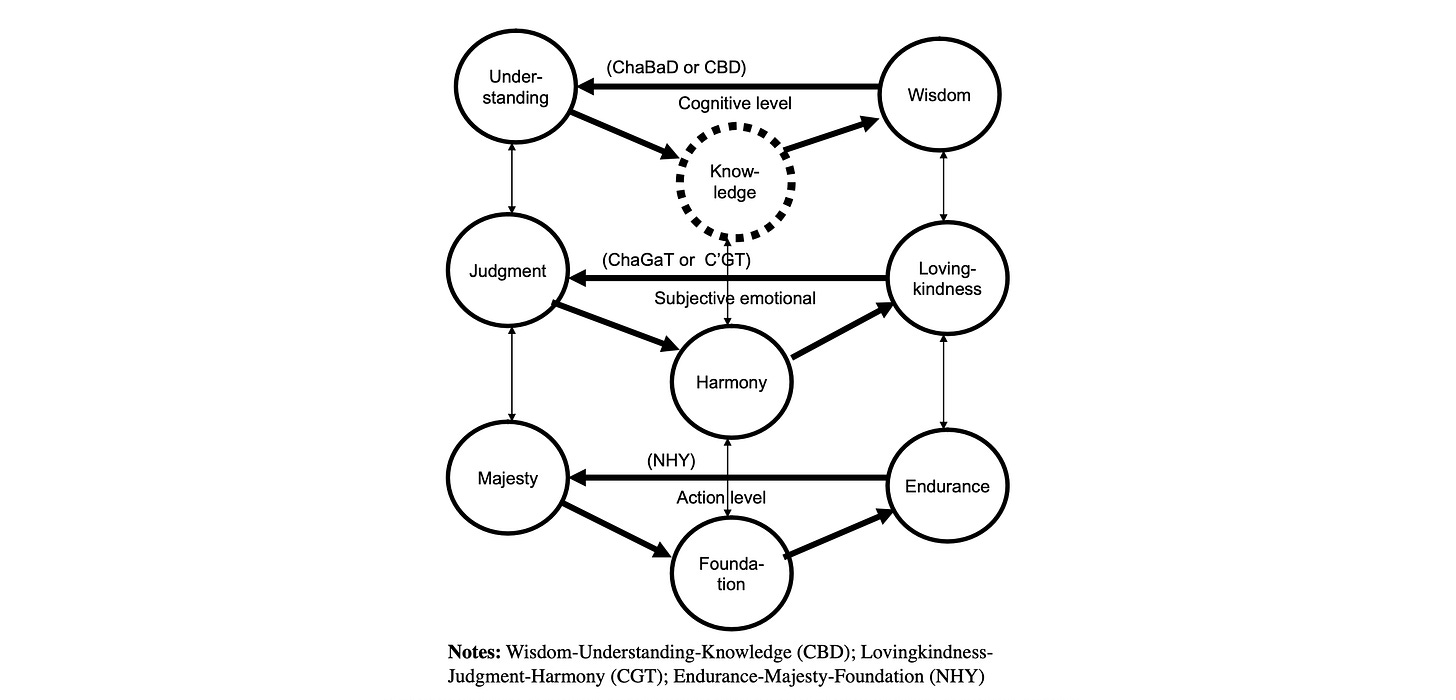
The core of KST is the ‘Tree of Life’, treated as a structural model with three hierarchical triadic levels, each serving distinct functions in system control:
Cognitive Level (ChaBaD)
In KST, this level is composed of Keter (Crown), Chochmah (Wisdom), Binah (Understanding), and Da’at (Knowledge). The papers describe this as the knowledge and cognitive level where understanding is formed and structured.
In infrastructure terms, this corresponds to stable configuration and low-frequency information processing where:
Entities and rules are recognised and catalogued
Standards and frameworks are defined
Knowledge is structured for operational use
Meta-level objectives and policies are set
The cognitive level establishes ‘what is’ and ‘what should be’ — the foundational configuration that other levels reference.
Emotional Level (ChaGaT)
In KST, this level is composed of Chesed (Lovingkindness), Gevurah (Judgment), and Tiferet (Harmony). The papers describe this as handling emotional and evaluative responses, with the midline sefira Tiferet serving as the feedback controller balancing the other two.
Functionally, this corresponds to continuous evaluation and high-frequency information processing:
Chesed: continuous receptive monitoring, data acceptance
Gevurah: rigorous compliance checking, judgment functions
Tiferet: balanced assessment, system stability evaluation
The emotional level continuously evaluates whether the system is operating according to the cognitive layer’s configuration.
Behavioural Level (NHY)
In KST, this level is composed of Netzach (Endurance), Hod (Majesty/Splendor), Yesod (Foundation), and Malkuth (Kingship). The papers describe this as the physical action and behavioural level, with Yesod serving as the controller.
Functionally, this corresponds to discrete execution and irreversible actions:
Netzach: outbound processing to subsystems
Hod: inbound responses from subsystems
Yesod: actuation and control signal integration
Malkuth: final output and settlement
The behavioural level executes actions only after passing through cognitive configuration and emotional evaluation.
The papers emphasise that these levels are hierarchically linked through feedback loops — information flows upward (monitoring informs knowledge), while control flows downward (knowledge configures evaluation, evaluation gates action). This bidirectional flow is essential to the architecture.
1.2. Information Frequency as Architectural Principle
While KST itself does not formulate the hierarchy in terms of ‘signal frequency’, this lens is consistent with control theory and makes its three-level decomposition functionally intelligible. The question becomes: what makes this structure necessary rather than arbitrary?
The answer lies in information frequency — the rate at which different types of information change and must be processed.
Low-Frequency Information (Cognitive)
Some information is stable: who entities are, what standards apply, who’s eligible to participate. This information:
Changes rarely (entities don’t change identity frequently, standards evolve slowly)
Is referenced constantly (every transaction must verify identity, every action must check standards)
Must be authoritative (conflicting identity claims or standards create system failure)
Low-frequency information naturally structures as registries: authoritative catalogues that are updated infrequently but queried continuously. The cognitive layer maintains these registries.
High-Frequency Information (Emotional)
Other information is dynamic: compliance status, performance metrics, system health. This information:
Updates constantly (every transaction generates new data, compliance status changes with each action)
Requires continuous evaluation (rules must be checked in real-time, not periodically)
Determines immediate decisions (actions are permitted or blocked based on current state)
High-frequency information naturally structures as monitoring systems: continuous evaluation streams that assess compliance, track performance, and verify adherence to standards defined in the cognitive layer. The emotional layer implements this monitoring.
Discrete Events (Behavioural)
Finally, some information represents irreversible state changes: contracts signed, payments settled, authority transferred. This information:
Occurs as discrete events (there’s a clear before and after)
Cannot be undone (settlement is final, contracts are binding)
Requires clear accountability (who authorised what action and when)
Discrete events naturally structure as execution gates: conditional release mechanisms that trigger irreversible actions only when monitoring (emotional layer) confirms compliance with configuration (cognitive layer). The behavioural layer controls these gates.
In such a hierarchical design, monitoring is parametrised by registry decisions, and execution is gated by monitoring outcomes. This dependency structure is what makes the three-level hierarchy operationally coherent.
1.3. From Frequency to Roles: The Ten Functional Positions
Information frequency determines data structure. The three levels unfold into ten distinct functional roles (which in later analysis often aggregate into higher-level ‘rails’). Here we map each KST component to its infrastructural interpretation:
Cognitive Layer → Registries (Low-Frequency)
Keter (Standards/Policy Mandate)
KST definition: Crown, will, desire, meta-knowledge
Infrastructural interpretation: Meta-level rules defining system objectivesFunction: Top-level policy frameworks, regulatory mandates, system goals
Example: Basel III capital requirements, UN Sustainable Development Goals, central bank mandates
Why here: Meta-governance changes rarely but determines everything downstream
Chochmah (Identity)
KST definition: Wisdom, tacit knowledge, ideas
Infrastructural interpretation: Recognition of entitiesFunction: Who/what exists in the system, entity recognition
Example: Digital ID systems, PKI certificates, entity registries
Why here: Identity is the fundamental ‘wisdom’ of knowing who is who — stable but constantly referenced
Binah (Accreditation)
KST definition: Understanding, explicit knowledge
Infrastructural interpretation: Evaluation of entities against standardsFunction: Determining which entities meet eligibility criteria
Example: Vendor pre-qualification lists, authority vetting, accreditation frameworks
Why here: ‘Understanding’ which entities satisfy standards defined by Keter — updated periodically, not continuously
Da’at (Compiled Registry/Model)
KST definition: Knowledge, practical relevance, serves as interface between cognitive and emotional levels, described as containing an internal model of the system
Infrastructural interpretation: Operational knowledge baseFunction: Integrated database that the monitoring layer queries
Example: The actual compiled registry combining identity + standards + accreditation
Why here: The papers explicitly connect Da’at to the internal model principle from control theory — it’s the cognitive layer’s model of the system that the emotional layer uses for evaluation
Emotional Layer → Monitoring (High-Frequency)
Chesed (Continuous Monitoring/Data)
KST definition: Lovingkindness, giving, accepting, expressing
Infrastructural interpretation: Constant receptive attentionFunction: Data ingestion, telemetry streams, performance tracking
Example: KPI dashboards, transaction monitoring, system telemetry
Why here: In KST’s emotional level, Chesed represents acceptance and receptivity; functionally, this corresponds to continuous data collection
Gevurah (Continuous Audit)
KST definition: Judgment, strength, rigor, discipline, rejection
Infrastructural interpretation: Rigorous compliance verificationFunction: Real-time/ongoing compliance checking, certification verification
Example: Audit systems, rule enforcement, compliance scoring
Why here: In KST’s emotional level, Gevurah represents judgment and rigor; functionally, this corresponds to continuous compliance checking
Tiferet (System Health/Stability)
KST definition: Harmony, beauty, balance, midline controller between Chesed and Gevurah
Infrastructural interpretation: Balanced assessmentFunction: Integrated health indicators, resilience metrics, balanced evaluation
Example: System stability dashboards, resilience scores, overall health assessment
Why here: The papers describe Tiferet as the feedback controller balancing the emotional level; functionally, this corresponds to integrated system health assessment
Behavioural Layer → Execution (Discrete Events)
Netzach (Processing to Child Holons)
KST definition: Endurance, perseverance, continuity
Infrastructural interpretation: Outbound coordinationFunction: Commands, queries, coordination signals to subsystems
Example: API calls to lower-level systems, instruction propagation, command distribution
Why here: KST places Netzach in the behavioural action level; the ‘endurance’ aspect suggests continuous outbound flow
Hod (Receiving from Child Holons)
KST definition: Splendor, acknowledgment, discrete occurrences
Infrastructural interpretation: Inbound responsesFunction: Status reports, completion acknowledgments, outcome data from subsystems
Example: Response messages, event notifications, child system reports
Why here: KST places Hod in the behavioural level; the occurrence/acknowledgment aspect suggests discrete inbound events
Yesod (Actuation)
KST definition: Foundation, channeling, renewal, preparation; explicitly described as controller for the behavioural level
Infrastructural interpretation: Control signal integrationFunction: Decision to release control signal that triggers execution
Example: Tranche release authorisation, payment instruction, contract approval
Why here: The papers identify Yesod as the feedback controller that channels integrated decisions into action
Malkuth (Output/Settlement)
KST definition: Kingship, manifestation, physical implementation
Infrastructural interpretation: Final manifestationFunction: Irreversible state change, settlement finality
Example: Payment execution, asset transfer, contract binding, authority transfer
Why here: KST describes Malkuth as the physical manifestation level—the final output
1.4. The Recursive Structure: Child Holons
The papers emphasise that the Tree of Life has a fractal, inter-inclusive structure — each sefira contains within it a sub-Tree of Life with its own ten components. While they don’t fully formalise holonic input-output protocols, KST’s discussion of the ‘four worlds’ and its recursive decomposition strongly suggests a holonic view: each subsystem reproduces the tri-level pattern and connects via interface points.
This recursion becomes operationally legible in the Netzach/Hod pairing, which can be read as representing the interface between parent and child holons:
Netzach = Parent’s outbound commands to child systems
Hod = Parent’s inbound responses from child systems
Each holon (self-contained system unit) would then have:
Its own cognitive layer (local registries)
Its own emotional layer (local monitoring)
Its own behavioural layer (local execution)
Interfaces via Netzach/Hod equivalents to parent and child holons
This interpretation explains how the same architecture would repeat at every scale:
Global scale: International standards → National implementations → Local transactions
National scale: Central bank rules → Commercial banks → Individual accounts
Transaction scale: Compliance check → Authorisation → Settlement
At each level, Malkuth’s output (settlement/finality) becomes input to the parent level’s Hod (inbound data), which feeds into the parent’s Chesed (monitoring), potentially updating the parent’s Da’at (compiled model), which may influence future Yesod (actuation) decisions.
This recursive feedback loop across scales is what hierarchical control systems require to maintain coherence.
1.5. The Complete Control Flow
Integrating all components, the architecture operates as follows:
Configuration Phase (Cognitive)
Keter defines meta-standards (policy objectives, system goals)
Chochmah identifies entities (who exists, entity recognition)
Binah accredits entities (who’s eligible, evaluation against standards)
Da’at compiles operational model (queryable integrated registry)
Evaluation Phase (Emotional)
Chesed monitors system state (continuous data ingestion)
Gevurah audits compliance (rigorous rule checking)
Tiferet assesses stability (balanced health evaluation)
Execution Phase (Behavioural)
Netzach processes to child holons (sends commands, propagates queries)
Hod receives from child holons (gets responses, collects events)
Yesod actuates (integrates signals, releases control)
Malkuth outputs (executes settlement, manifests final state)
Feedback Loop
Malkuth’s output feeds back into:
Parent holon’s Hod (becomes input to higher level)
Own level’s Chesed (monitoring observes outcome)
Updates to Da’at registry (learning and adaptation)
In this architecture, monitoring is parametrised by registry decisions, and execution is gated by monitoring outcomes. Each layer depends on the one above it. This dependency structure is not decorative — it’s what makes conditional control at scale operationally coherent.
1.6. Mathematical Formalisation
The papers ground this framework in category theory and control engineering:
Pullback operations model aggregation: how information from multiple sources (Chochmah and Binah) combines at Da’at to create the operational model that the emotional layer queries.
Pushout operations model system coupling: how child holons integrate into parent holons, and how feedback from execution (Malkuth) propagates back to update monitoring (Chesed) and configuration (Da’at).
Internal model principle from control theory: The papers explicitly connect Da’at to Wonham’s internal model principle — a robust controller must contain an internal model of the system it controls. Da’at serves precisely this role: it’s the cognitive layer’s model of the system that the emotional layer uses for evaluation.
Hierarchical feedback control: The three levels form a feedback control system where:
Cognitive configures (feedforward)
Emotional evaluates (feedback)
Behavioural executes (control action)
Results feed back to cognitive (adaptation)
This isn’t metaphysics — it’s formalised control theory mapped to system architecture.
1.7. The Seven Rails: Aggregated View
For practical analysis, the ten functional positions can be aggregated into seven operational ‘rails’ — the technical systems through which conditional control is implemented:
Standards (Keter)
Policy frameworks and meta-governance.Identity (Chochmah)
Entity recognition and registration.Accreditation (Binah)
Eligibility and authority determination.Data (Chesed)
Continuous monitoring and collection.Audit (Gevurah)
Compliance verification and enforcement.Coordination / IO (Netzach/Hod)
Execution coordination with subsystems: outbound obligations, inbound reports, scheme rules, and messaging.Actuation & Settlement (Yesod/Malkuth)
Triggers, control signals, and irreversible execution (payments, transfers, final states).
Da’at (compiled model) and Tiferet (stability assessment) operate as integration layers rather than distinct rails — they synthesise information from other components.
This seven-rail view makes the architecture easier to map to observable infrastructure while preserving the underlying ten-component structure.
1.8. Why This Framework Matters
KST provides systematic decomposition for analysing complex control systems. Given any hierarchical control infrastructure, you can now ask precise diagnostic questions:
Registry layer questions:
What meta-standards govern the system? (Keter)
How is identity established and verified? (Chochmah)
How is eligibility determined? (Binah)
What compiled model does monitoring query? (Da’at)
Monitoring layer questions:
What data is continuously collected? (Chesed)
What compliance rules are checked in real-time or near real-time? (Gevurah)
How is system stability assessed? (Tiferet)
Execution layer questions:
How are commands propagated to child systems? (Netzach)
How are responses collected from child systems? (Hod)
What triggers execution decisions? (Yesod)
What constitutes final settlement? (Malkuth)
System-wide questions:
Where do feedback loops exist?
Where can control concentrate?
Where could failures cascade?
How many recursion levels exist?
This framework makes opaque systems legible and auditable.
1.9. Setting Up the Convergence
The Burstein/Negoița papers were published between 2011 and 2016, establishing this complete theoretical framework. The papers applied KST to behavioural economics, knowledge engineering, artificial intelligence, and complex systems modeling — theoretical domains where hierarchical control with human decision-making elements was analytically important.
What the papers did not examine in depth was concrete financial market and payment infrastructure design.
In 2019, the Bank for International Settlements established its Innovation Hub. Between 2020 and 2024, this Hub developed and deployed a series of modular projects for programmable money, cross-border settlement, and tokenisation. These projects were designed by different teams, in different jurisdictions, addressing different technical problems.
When read structurally, these projects line up with the KST architecture with striking fidelity.
This is the convergence we now examine.
2. From Abstract Control to Concrete Governance: Operational Semantics
The Tree of Life’s ten sefirot function as abstract control components. To analyse real-world systems, we require operational semantics — specifications mapping each sefira to concrete governance functions. This section establishes those mappings, transforming KST from theoretical framework to analytical instrument.
2.1 Keter: Standards and Policy Grammar
Function: Establish normative objectives, define system boundaries, set the ‘grammar’ for legitimate action.
Governance Manifestation:
Constitutional principles and founding treaties
Strategic frameworks (UN SDGs, national security strategies)
Central bank mandates and stability objectives
Rulebooks defining what the system optimises for
Key Property: Keter is often opaque or externalised. In recursive structures, a child holon’s Keter receives constraints from its parent’s Netzach, limiting local autonomy.
Observed Examples:
UN Charter and SDG framework (global)
BIS Agorá unified ledger rulebook (financial infrastructure)
EU Treaties and integration objectives (regional)
National constitutions and legislative mandates (national)
2.2 Chochmah: Identity and Recognition
Function: Identify subjects, recognise entities, establish ‘who/what exists’ in the system’s ontology.
Governance Manifestation:
Digital identity systems (e-KYC, national ID, biometrics)
Entity recognition (corporate registries, NGO accreditation)
Citizenship and residency status
Access control lists
Key Property: Chochmah determines eligibility before any action occurs. Without recognition, an entity cannot participate.
Observed Examples:
BIS Sela: minimal-trust identity roles for retail CBDC
UNDP Digital Public Infrastructure identity systems
e-KYC in financial services
Passport and visa systems
2.3 Binah: Accreditation and Institutional Form
Function: Classify recognised entities into categories, assign capabilities and permissions, define institutional structures.
Governance Manifestation:
Licensing regimes (banking licenses, professional credentials)
Tiered access systems (retail vs. wholesale financial participants)
Organisational mandates (ministry portfolios, agency authorities)
Legal categorisation (public/private, profit/non-profit)
Key Property: Binah structures the operational space — defining roles and what each role can do.
Observed Examples:
BIS Aurum: two-tier CBDC with institutional roles
Banking license categories and prudential requirements
UN agency mandates and accreditation
Professional licensing boards
2.4 Da’at: Models and Indicators
Function: Synthesise standards (Keter), identities (Chochmah), and structures (Binah) into operational models. Define KPIs, thresholds, risk metrics, decision rules.
Governance Manifestation:
KPI frameworks and scorecards
Risk assessment models
Econometric and simulation models
Logical frameworks (logframes) in project management
Smart contract conditions
Key Property: Da’at is where policy becomes computable — transforming normative goals into measurable criteria and executable logic.
Observed Examples:
BIS Mandala: jurisdiction-specific regulatory requirements encoded in protocol
UN SDG indicator framework: 231 indicators tracking progress
RBM logical frameworks: inputs → outputs → outcomes → impact
Credit scoring models and risk matrices
2.5 Chesed: Telemetry and Observability
Function: Continuously collect data from operations, monitor system state, create visibility.
Governance Manifestation:
Real-time dashboards and scoreboards
Surveillance systems (transaction monitoring, border controls)
Reporting requirements (financial filings, progress reports)
Sensor networks and IoT infrastructure
Supervisory technology (SupTech)
Key Property: Chesed is expansive observation — the data lake feeding decision-making. Without it, the system is blind.
Observed Examples:
BIS Pyxtrial: near-real-time stablecoin monitoring
BIS Ellipse: SupTech early warning platform
Financial transaction monitoring systems
UNDP M&E units
2.6 Gevurah: Audits and Gates
Function: Enforce constraints, perform compliance checks, apply sanctions, implement gatekeeping.
Governance Manifestation:
Eligibility verification before disbursement
Sanctions screening
Audit triggers and enforcement actions
Conditional assistance mechanisms
Capital controls and transaction limits
Key Property: Gevurah is restrictive power — saying ‘no’ when thresholds breach. In programmable systems, Gevurah gates operate at transaction speed.
Observed Examples:
BIS Tourbillon: privacy/security constraints with tiered surveillance
Conditional cash transfer eligibility verification
World Bank safeguards frameworks
Sanctions screening in payment systems
2.7 Tiferet: Optimisation and Balance
Function: Maintain stability, optimise across competing objectives, manage trade-offs, coordinate between expansion (Chesed) and constraint (Gevurah).
Governance Manifestation:
Budget allocation algorithms
Portfolio management and asset-liability matching
Automated Market Makers in DeFi
Macroprudential policy frameworks
Multi-objective optimisation in planning
Key Property: Tiferet sits on the middle pillar, mediating extremes. It’s the system’s executive function — balancing conflicting demands.
Observed Examples:
BIS Mariana: Automated Market Maker for cross-border FX using wholesale CBDC
PPBS program budgeting: resource allocation across programs
Central bank monetary policy: balancing inflation and growth
Multi-criteria decision analysis in development planning
2.8 Netzach: Outbound Commands
Function: Deliver persistent instructions to subordinate entities, implement programs, push resources and directives downward.
Governance Manifestation:
Grant and loan disbursements
Policy directives from higher to lower administrative levels
Program launches and campaign execution
Service delivery pipelines
Key Property: Netzach is the outbound interface. In a holarchy, a parent’s Netzach connects to children’s Keter, cascading commands down the hierarchy.
Observed Examples:
BIS Nexus: connecting domestic instant payment systems
BIS Icebreaker: retail CBDC corridors
World Bank program funding to implementing agencies
Policy directives federal → state → local
2.9 Hod: Inbound Reports
Function: Receive feedback from subordinate entities, validate compliance, aggregate performance data, enable upward accountability.
Governance Manifestation:
Reporting systems (quarterly reviews, M&E reports)
Recognition ceremonies and certifications
Consolidated financial statements
Compliance attestations
Key Property: Hod is the inbound interface. Children’s Malkuth (settled outcomes) feed into parent’s Hod, closing the feedback loop.
Observed Examples:
BIS Nexus: aggregating payment system data
UN agencies reporting to governing bodies
Financial consolidation from subsidiaries to parent
M&E reports from implementing partners to donors
2.10 Yesod: Coordination and Actuation
Function: Coordinate between operational units (Netzach and Hod), execute workflows, manage the ‘rails’ that make actions happen.
Governance Manifestation:
Payment and settlement systems
Workflow orchestration platforms
Smart contract execution layers
API gateways
Clearinghouses
Key Property: Yesod is the actuator — machinery translating decisions into material effects. In financial systems, it’s literally the payment rails.
Observed Examples:
BIS Rosalind: retail CBDC API layer with programmable locks
BIS Meridian: synchronisation between RTGS and DLT
SWIFT and correspondent banking networks
Digital Public Infrastructure payment rails (UPI, etc.)
Smart contract execution platforms
2.11 Malkuth: Settlement and Outcomes
Function: Record final outcomes, produce ground truth, manifest the system’s actual impact in the material world.
Governance Manifestation:
Ledgers and registries (land titles, transaction histories)
Physical deliveries (infrastructure built, vaccines administered)
Realised financial positions
Social outcomes (measured poverty rates, emissions levels)
Key Property: Malkuth is reality — what actually happened, as opposed to what was planned or reported. It’s the ultimate accountability anchor.
Observed Examples:
BIS mBridge: multi-CBDC platform for cross-border settlement (MVP 2024)
Blockchain and distributed ledger settlement
Land registries and property titles
UN SDG outcomes: measured poverty, health, education indicators
3. Recursive Holarchic Control: The Algorithm
We formalise the KST governance architecture as a recursive control loop. Each holon (autonomous unit) runs the same procedure, creating scale-free hierarchy.
3.1 Data Structures
struct Command
{
Objectives objectives; // What to achieve
Constraints constraints; // Boundaries and rules
Budget budget; // Available resources
string trace_id; // For audit trails
}
struct Outcome
{
Metrics metrics; // Measured results
Settlement settlement; // Actual material state
Provenance provenance; // Verification trail
string trace_id;
}3.2 The Control Loop
Each holon executes this procedure every control cycle (frame). This pseudocode is illustrative only; to ease comprehension, backward edges (loops) are not included:
function runFrame(holon, parentCommand):
// === COGNITIVE LAYER (Keter + ChaBaD) ===
// 1. KETER: Refine parent’s objectives into local policy
policy = holon.Keter.adapt(parentCommand)
// 2. CHOCHMAH: Identify relevant subjects/entities
identities = holon.Chochmah.recognise(policy)
// 3. BINAH: Structure institutions and roles
institutions = holon.Binah.accredit(policy, identities)
// 4. DA’AT: Build/update operational model
model = holon.Daat.synthesise(policy, identities, institutions)
// === EMOTIONAL LAYER (ChaGaT) ===
// 5. CHESED: Collect telemetry from previous frame
telemetry = holon.Chesed.observe()
// 6. GEVURAH: Enforce gates and constraints
holon.Gevurah.audit(telemetry, policy)
violations = holon.Gevurah.violations()
if violations.critical:
return FailureOutcome(violations)
// 7. TIFERET: Optimise plan for current frameplan = holon.Tiferet.optimise(model, telemetry, policy)
// === ACTION LAYER (NHY) ===
// 8. NETZACH: Generate commands for child holons
childCommands = holon.Netzach.derive(plan)
// 9. HOD: Collect outcomes from children (recursive call)
childOutcomes = []
for each child in holon.children:
outcome = runFrame(child, childCommands[child])
childOutcomes.append(outcome)
holon.Hod.validate(childOutcomes)
// 10. YESOD: Execute actuation based on plan + child results
execution = holon.Yesod.actuate(plan, childOutcomes)
// === SETTLEMENT ===
// 11. MALKUTH: Compute settled outcome
outcome = holon.Malkuth.settle(execution, parentCommand.trace_id)
return outcome3.3 Key Properties
Vertical Interfaces:
Downlink: Parent’s Netzach (step 8) → Child’s Keter (step 1).
Commands flow hierarchically down through this interface.Uplink: Child’s Malkuth (step 11) → Parent’s Hod (step 9).
Outcomes flow hierarchically up through this interface.
Horizontal Coordination: Within each holon, Yesod (step 10) coordinates between Netzach (outbound) and Hod (inbound), preventing oscillations.
Audit Trail: trace_id propagates through the execution tree, enabling end-to-end provenance from global policy down to individual transactions.
Failure Modes:
Gevurah gate failure: Child violates constraints; parent receives failure outcome and may withhold resources or impose sanctions.
Hod validation failure: Child reports are inconsistent; parent may escalate to audit or enforce penalties.
Yesod actuation failure: Execution rails fail; outcomes don’t settle properly, triggering Malkuth discrepancy detection.
Recursion Depth: The algorithm is scale-free. A global financial institution might have:
Level 0: BIS / Central Banks (global coordination)
Level 1: National monetary authorities
Level 2: Commercial banks
Level 3: Bank branches or business units
Level 4: Individual customer accounts
Level 5: Individual transactions
Each level runs the same 11-step procedure with consistent interfaces.
Historical Connection: This recursive structure directly implements multi-level clearing logic pioneered by the London Clearing House in the 19th century. Modern CBDC architectures (mBridge, Agorá) extend this recursive clearing principle globally, making it programmable (smart contract conditions at every level) and real-time (settlement in seconds rather than days).
4. Observed Implementations: Progressive Architectural Completion
We document that major governance systems exhibit structural patterns analysable through the KST framework. Rather than coincidental partial overlaps, we observe systematic progression toward architectural completeness.
4.1 Planning-Programming-Budgeting Systems (PPBS): The Skeleton
Background: Developed in the 1960s by RAND Corporation and implemented across U.S. federal agencies, PPBS introduced systematic analysis and long-term planning into government budgeting.
KST Mapping:
PPBS Component Sefirot Function
———————————————————— ————————— ————————————————————————————————————
Strategic objectives Keter Top-level goals (national security,
welfare)
Program categories Binah Institutional structure (defense,
health, education)
Systems analysis Da’at Modeling costs, effectiveness,
alternatives
Program budgeting Tiferet Resource allocation across programs
Budget execution Yesod Appropriations and disbursements
Program review Gevurah Audit and evaluation———————————————————— ————————— ————————————————————————————————————Gap Analysis: PPBS partially implemented the middle column (Da’at–Tiferet–Yesod) but lacked:
Dense Chesed: Limited real-time data collection; relied on periodic reports
Granular Gevurah: Weak automated enforcement; gates were administrative, not algorithmic
Explicit Netzach/Hod: Poor recursion between federal, state, and local levels
Clear Malkuth: Focused on spending rather than outcomes
Significance: PPBS demonstrated viability of systematic control architecture but was incomplete as a KST implementation.
4.2 Results-Based Management (RBM): The Nervous System
Background: Emerged in the 1990s as ‘New Public Management’ reform, emphasising measurable results, performance indicators, and accountability. Widely adopted by international development organisations (World Bank, UNDP, bilateral donors).
KST Mapping:
RBM Component Sefirot Function
———————————————————————— ————————— ————————————————————————————————
Logical frameworks Da’at Inputs → Outputs → Outcomes
(logframes) → Indicators
Performance indicators Da’at/ What to measure +
(KPIs) Chesed measurement systems
Monitoring & Evaluation Chesed/ Data collection + reporting
(M&E) Hod
Conditional disbursement Gevurah Gates based on perf. thresholds
Scorecards and dashboards Chesed Visibility of performance
————————————————————————— ————————— ————————————————————————————————Advancement Over PPBS: RBM strengthened:
Da’at: Explicit indicator frameworks made policy computationally legible
Chesed: Routine monitoring created continuous telemetry
Gevurah: Performance-based funding introduced algorithmic gates
Remaining Gap: RBM improved the cognitive and emotional layers but still relied on manual processes for Yesod (disbursement workflows) and lacked programmable actuation.
Synthesis: PPBS + RBM approximates a more complete KST cognitive and emotional layer. The missing piece was the action layer infrastructure — digital rails for automated execution.
4.3 Bank for International Settlements Innovation Hub: The Complete Stack
Background: The BIS Innovation Hub, established in 2019, conducts experimental projects exploring central bank digital currencies (CBDCs), tokenisation, and programmable money. Multiple projects collectively exhibit a comprehensive control architecture.
Complete KST Mapping:
Project Sefirot Function
———————————————— ————————- ————————————————————————————————————————
Agorá Keter Unified ledger rulebook; policy grammar
for tokenised deposits + wCBDC
Sela Chochmah Minimal-trust identity roles for retail
CBDC access
Aurum Binah Two-tier CBDC with institutional roles
Mandala Da’at Encodes jurisdiction-specific regulatory
requirements into common protocol
Pyxtrial/Ellipse Chesed Near-real-time stablecoin monitoring;
SupTech early warning platform
Tourbillon Gevurah Privacy/security constraints; tiered
surveillance
Mariana Tiferet AMM for cross-border FX using wCBDC
Nexus/Icebreaker Netzach/ Connect domestic instant payment
Hod systems; CBDC corridors
Rosalind/Meridian Yesod Retail CBDC API layer; RTGS–DLT
synchronisation
mBridge Malkuth Multi-CBDC platform for cross-border
settlement (MVP 2024)
———————————————— ————————- ————————————————————————————————————————Analysis:
Completeness: Every sefira corresponds to at least one project or capability. This constitutes de facto comprehensive architectural coverage.
Vertical Spine: The middle pillar (Keter → Da’at → Tiferet → Yesod → Malkuth) is fully operational:
Agorá sets grammar
Mandala compiles into rules
Mariana optimises
Rosalind/Meridian execute
mBridge settles
Pillars:
Constraint: Binah (Aurum) → Gevurah (Tourbillon) → Hod (Nexus inbound)
Expansion: Chochmah (Sela) → Chesed (Pyxtrial/Ellipse) → Netzach (Nexus/Icebreaker outbound)
Recursion: The architecture supports hierarchical deployment:
Global: BIS/central banks coordinate
National: Each central bank issues CBDC within Agorá grammar
Commercial: Banks participate via defined roles (Binah)
Retail: Individuals access via wallets with Sela-style identity
Observation: The BIS Innovation Hub is systematically building infrastructure exhibiting all 10 sefirot as operational components — a complete KST stack for global programmable money. BIS itself increasingly presents these initiatives not as isolated pilots but as coordinated ‘building blocks’ of a unified-ledger-based future monetary system and a global ‘Finternet’, where tokenised money, assets, identity and compliance operate on integrated platforms under common governance.
4.4 United Nations Development System: Global Framework
Background: The UN Sustainable Development Goals (SDGs) and associated Results-Based Management frameworks structure development assistance globally.
KST Mapping:
UN System Component Sefirot Function
—————————————————————— ——————— ————————————————————————————————————SDGs Keter 17 global objectives by 2030
SDG indicator framework Da’at 231 indicators for tracking progress
National development Da’at Countries adapt SDGs into local
plans (child) context
UNDP/Agency monitoring Chesed Data collection through country
offices
Safeguards & compliance Gevurah Environmental, social,
governance standards
Programme funding Netzach Disbursement to implementing agencies
Agency reporting Hod Reports to governing bodies
Digital Public Yesod ID systems, payment rails (MOSIP,
Infrastructure UPI, etc.)
Development outcomes Malkuth Measured poverty, health, education
changes
—————————————————————— ——————— ————————————————————————————————————Holarchic Levels:
Global: UN General Assembly / Secretary-General
Regional: UNDP regional bureaus, development banks
National: Governments and UN Country Teams
Sectoral: Ministries and specialised agencies
Programmatic: Individual projects and NGOs
Observation: The SDG framework exhibits KST architecture globally. A notable development has been strengthening Yesod (execution infrastructure) through Digital Public Infrastructure initiatives.
4.5 Synthesis: Progressive Completion
The historical progression reveals systematic architectural development:
1960s PPBS:
[K] --- [D] --- [T] --- [Y] --- [ ]
Skeleton: Middle column only1990s RBM:
[K] [C] [D] --- [T] --- [Y] --- [ ]
[Cs][G]
Nervous system: Added monitoring/gates2019–2024 BIS:
[K] [C] [D] [C’][T] [N] [Y] [M]Complete: All sefirot operational
[B] [Cs][G] [H]
Each generation added missing components:
PPBS: cognitive spine (Keter, Da’at, Tiferet)
RBM: monitoring and gates (Chesed, Gevurah)
BIS Hub: action infrastructure (Yesod, Malkuth)
What arrives in 2024 is not a wholly new system but the completion of a long-running architectural trajectory. The BIS Innovation Hub does not invent governance from scratch — it provides the digital rails that make existing control logic executable at transaction speed. Where PPBS and RBM operated at the macro level of plans, programmes, and aggregated indicators, CBDC and unified-ledger infrastructures instantiate the same control grammar at the micro level of individual identities and transactions, closing the loop between high-level governance design and point-of-use enforcement for the average citizen.
5. The Emergency Architecture: Qliphothic Inversion
5.1 The Shadow Tree: Normal and Emergency Modes
In Kabbalistic tradition, the qliphoth (singular: qliphah, ‘husks’ or ‘shells’) represent the shadow or inverted Tree of Life. Each sefira has a corresponding qliphothic aspect — a degraded or inverted manifestation of its function.
From a systems perspective, the qliphothic state represents emergency mode: when normal control hierarchies invert, recursion breaks down, and the system operates under exception logic.
Qliphothic Correspondences:
Sefira (Normal) Qliphah (Inv) Emergency Manifestation
————————————————————— ——————————— —————————————————————————————————
Keter (Standards) Thaumiel Competing emergency authorities;
martial law
Chochmah (Recognition) Ghagiel Identity suspension; ‘enemy
combatant’ categories
Binah (Structure) Satariel Black box decision-making;
classified procedures
Da’at (Knowledge) (none) Model collapse; ‘unknown unknowns’
Chesed (Observation) Gamchicoth Total surveillance; panopticon
activation
Gevurah (Constraint) Golachab Collective punishment;
automated kill decisions
Tiferet (Balance) Thagirion Optimisation failure; thrashing
between extremes
Netzach (Outbound) A’arab Zaraq Command breakdown; fragmented
authority
Hod (Inbound) Samael False reporting; propaganda as
feedback
Yesod (Coordination) Gamaliel Execution without coordination;
atrocity
Malkuth (Outcomes) Nehemoth Catastrophic ground truth;
humanitarian disaster
————————————————————— ——————————— —————————————————————————————————5.2 Triggering the Inversion: States of Exception
The qliphothic architecture activates under conditions Agamben describes as the ‘state of exception’ — when normal law suspends and sovereign power operates directly.
Trigger Conditions:
Complex Global Shock (natural disaster, pandemic, financial crisis, conflict)
Computational Intractability (normal optimisation fails; Da’at cannot model)
Legitimacy Crisis (democratic processes too slow for perceived threat)
Systemic Cascade (failures propagating faster than normal control can respond)
Architectural Transformation:
Normal mode (Tree of Life):
Keter (democratic mandate)
↓
ChaBaD (deliberative analysis)
↓
ChaGaT (balanced trade-offs)
↓
NHY (accountable execution)
↓
Malkuth (measured outcomes)
Emergency mode (Qliphothic inversion):
Thaumiel (emergency executive power)
↓
Satariel (classified decision-making)
↓
Gamchicoth–Golachab (total surveillance + automated enforcement)
↓
Gamaliel (uncoordinated execution)
↓
Nehemoth (catastrophic outcomes)
Key Property: The inversion doesn’t eliminate the architecture — it runs the same algorithm with inverted values:
Keter → Thaumiel: Standards become emergency decrees
Chesed → Gamchicoth: Observation becomes total surveillance
Gevurah → Golachab: Constraint becomes collective punishment
Yesod → Gamaliel: Coordination becomes unaccountable execution
The structure remains, but feedback inverts: instead of outcomes informing policy refinement, emergency powers justify their own expansion.
5.3 UN Emergency Platform: Architecturally Equivalent Mode-Switch Mechanism
Background: In September 2024, the UN Secretary-General’s report Strengthening the international response to complex global shocks proposed an Emergency Platform — a mechanism for rapid response to crises exceeding normal institutional capacity.
Stated Function:
Convene stakeholders rapidly during complex global shocks
Coordinate across UN system, governments, private sector
Enable ‘more coherent, effective, and better-resourced’ responses
Structural Analysis:
The Emergency Platform exhibits architectural properties consistent with a pre-authorised mechanism for operational mode-switching from normal to emergency governance:
Normal Condition Emergency Platform Structural Property————————————————————— —————————————————————— ————————————————————————
Keter (UN Charter, ‘Complex global shock’ Ambiguous triggering;
sovereignty) competing authorities
Da’at (transparent Convening mechanism Decision procedures w/o
models) (opaque criteria) specified parameters
Chesed (normal ‘Enhanced data Surveillance
monitoring) sharing’ intensification
Gevurah (due process ‘Streamlined Constraint removal
constraints) decision-making’ justified by urgency
Tiferet (balanced ‘Rapid Speed prioritised
optimisation) coordination’ over deliberation
Yesod (accountable ‘Private sector Execution authority w/o
execution) engagement’ standard accountability
————————————————————— —————————————————————— ————————————————————————Architectural Observation:
The Platform’s design exhibits underspecified activation and deactivation conditions:
No formal criteria define ‘complex global shock’ requiring activation
Authority to trigger the Platform is not explicitly designated
Powers exercised under activation are not enumerated
Duration of emergency authorities is not bounded
Safeguards preventing scope expansion are not specified
This design pattern is architecturally consistent with a standing mode-switch mechanism — an infrastructure that can enable transition from normal (Tree of Life) to emergency (qliphothic) operational modes without requiring explicit new authorities. The authorisation logic exists; only triggering conditions remain to be invoked.
Historical Context: The Platform builds on crisis precedents where normal governance structures were suspended:
COVID-19 response (lockdowns, surveillance, emergency spending)
2008 financial crisis (central bank emergency authorities)
Post-9/11 security measures (surveillance, detention)
Each crisis established qliphothic capabilities that persisted after the emergency ‘ended’. The Platform documents this inversion as governance architecture.
5.4 Case Study: Conditional Sovereignty in Practice
Ukraine Facility (European Union): Adopted December 2023, provides up to €50 billion over 2024–2027, explicitly conditioned on reform implementation.
Holarchic Structure:
EU (parent holon):
Netzach: Disburse funds + technical assistance
Hod: Receive and validate reform reports
Gevurah: €1.5B tranches released only after verified compliance
Ukraine (child holon):
Keter: Adapt EU objectives into national reform plan
Da’at: Define implementation benchmarks (reform scoreboard)
Chesed: Quarterly monitoring of progress
Netzach/Hod: Coordinate with ministries (sub-holons)
Yesod: Financial disbursement via EU instruments
Malkuth: Delivered institutional changes
Ukrainian Ministries (grandchild holons):
Each ministry runs its own KST loop to implement sectoral reforms
Observation: The Ukraine Facility exhibits conditional fiscal sovereignty through KST architecture. The parent (EU) retains gatekeeping power (Gevurah) over a child holon’s (Ukraine) fiscal resources, while the child maintains operational autonomy within defined constraints. This represents the architecture functioning in normal (Tree of Life) mode with accountability mechanisms intact.
The same structural pattern can operate in emergency mode with accountability inverted. When combined with programmable infrastructure (digital ID, CBDC, conditional assistance frameworks), this architecture enables what can be termed conditional access architecture — where rights (movement, employment, property, services) become programmable via digital infrastructure, with gatekeeping controlled by parties who set the measurement criteria.
A similar architecture is already taking shape in the Gaza reconstruction proposals. Donors and an externally led transitional authority define reform and security conditions and retain control over disbursement and project selection (Keter/Binah/Netzach), with reconstruction finance gated in tranches against externally verified benchmarks and audits (Gevurah/Hod), and implementation channelled through standardised UN/IFI procurement regimes, vetted vendors, and existing humanitarian digital ID and registration systems (Chochmah/Yesod/Malkuth). The same holarchic logic appears: conditional sovereignty flowing from conditional finance, enforced through six converging rails — accreditation, finance, digital ID, audits, data, and procurement — such that access to reconstruction, services, and livelihoods can be made contingent on enrolment, compliance, and visibility within externally governed infrastructures.
In structural terms, Gaza functions as a compressed demonstration of the same conditional access architecture: humanitarian and reconstruction language at the top, infrastructural gatekeeping determining what is materially possible on the ground.
5.5 Black Box Models and Computational Legitimation
Black Box Decision-Making refers to algorithmic systems where:
Inputs are known (data fed to the model)
Outputs are observable (decisions produced)
Internal logic is opaque (proprietary, complex, or intentionally concealed)
In KST terms, this is Da’at collapse: the model (knowledge synthesis) becomes uninterpretable, yet decisions claiming to be ‘data-driven’ flow from it.
Manifestation in Governance:
Domain Black Box Qliphothic Function
——————————— ——————————————————— —————————————————————————————————————
Finance Credit scores, Satariel: Concealed risk models
algotrading determine access
Security Predictive policing Gamchicoth–Golachab:
watch lists Surveillance + automated sanction
Development AI-driven Thagirion: ‘Optimal’ decisions
allocation without transparency
Emergency ‘Complex shock’ Thaumiel: Who decides what triggers
detection emergency powers?
——————————— ——————————————————— —————————————————————————————————————The Legitimation Loop:
Complexity exceeds human comprehension
Experts claim only algorithmic models can manage it
Models become black boxes (‘proprietary’, ‘too complex’, ‘security’)
Decisions flow from black boxes, presented as neutral
Affected parties cannot contest internal logic
Failures justify more algorithmic control (‘we need better AI’)
This is Satariel legitimating Thaumiel: concealment justifies emergency authority.
Feedback Inversion:
Normal KST: Malkuth (outcomes) → Chesed (observe) → Tiferet (optimise) → Da’at (update model)
Qliphothic: Nehemoth (disaster) → Gamchicoth (intensify surveillance) → Thagirion (thrash) → Satariel (conceal model)
The architecture runs backward: instead of learning from outcomes, disasters justify opacity.
5.6 Implications of the Qliphothic Architecture
Permanence of Emergency
Once qliphothic architecture activates, it tends to persist:Surveillance (Gamchicoth) remains
Black box decision-making (Satariel) normalises
Expedited procedures (bypassing Tiferet) become default
Emergency authorities (Thaumiel) find new threats
Ratchet Effect
Each crisis adds capabilities that do not fully revert:Post-9/11: surveillance, detention, targeted killing
Post-2008: central bank emergency powers
Post-COVID: health passes, movement tracking
Post-2023: complex-shock platforms, AI governance, programmable money
Infrastructural Control Without Visible Coercion
Control shifts into infrastructure:Gates enforced by automated systems
Policy executes via code and platform rules
Logic concealed as proprietary or technical
Coercion appears as ‘terms of service’
Resistance Constraints
In a fully recursive qliphothic system:Voice → detected + sanctioned
Exit → blocked by ID/money rails
Loyalty → only viable path; criteria opaquely set
6. Convergent Evolution and Analytical Implications
6.1 Why the Structural Alignment Matters
The structural alignment between KST and real-world governance systems does not require claims about design intent. We observe convergent evolution: when institutions solve complex multi-scale control problems, they develop architectures exhibiting similar features.
Drivers:
Control theory fundamentals
Digital infrastructure affordances
PPBS → RBM → CBDC lineage
Optimisation pressure under crisis
Emergency ratchet effects
6.2 The Independent Discovery
Burstein and Negoita (2011–2016) developed KST in mathematical and computational domains, not as policy design. Meanwhile, BIS, UN, EU, etc. built practical systems which exhibit extraordinarily similar structural attributes. The convergence suggests KST captures recurring structural solutions to hierarchical control.
It is also notable, without implying design intent, that Burstein’s subsequent professional work has moved into digital assets and tokenisation, the same technical domain in which these architectures are now being operationalised. This reinforces the interpretation that KST identified a structural control grammar whose practical relevance extends into contemporary financial infrastructure.
6.3 Analytical Value of the KST Framework
Completeness checking (which sefirot/roles are missing)
Power concentration analysis (who owns Keter, Da’at, Gevurah, Yesod)
Recursion and scale (how policy reaches transactions)
Failure mode prediction
Emergency detection (when inversion patterns appear)
6.4 Alternative Architectures: Design Interventions
This section briefly outlines eight classes of interventions:
Open Da’at — Make models, indicators, and decision rules transparent and contestable so measurement and scoring cannot hide inside black boxes.
Plural Keter — Distribute standard-setting across multiple legitimate authorities to prevent a single, unaccountable source of meta-rules.
Local Yesod (multiple rails) — Maintain parallel execution and payment channels (cash, alternative networks) so no single rail can enforce total exclusion.
Human veto over Gevurah — Require explainability and human review for high-impact denials or sanctions instead of fully automated, unappealable gates.
Dense Hod (real upward accountability) — Strengthen bottom-up reporting, oversight, and audit so higher levels are structurally exposed to ground truth, not curated narratives.
Subsidiarity and recursion limits — Legally and technically cap how deep centralised control penetrates, preserving genuine autonomy at lower levels.
Emergency sunset clauses — Hard-code expiry, review, and re-authorisation requirements so exceptional powers cannot silently become permanent.
No enforcement without explainability — Forbid binding decisions whose operative logic cannot be inspected and challenged by those subjected to them.
Each weakens qliphothic lock-in at specific structural points.
7. Conclusion
This paper has:
Established operational semantics for each sefira as a governance function
Specified a recursive holarchic control algorithm
Documented structural alignment with PPBS, RBM, BIS IH, UN SDG, and conditional assistance mechanisms
Analysed emergency inversions via the qliphothic lens
The convergence pattern is clear: from clearing houses and PPBS to RBM and CBDCs, institutions independently assemble the same control skeleton KST formalises.
Central tension:
The same architecture that enables:
precise, real-time, evidence-based governance
also enables:
pervasive surveillance,
automated exclusion,
conditional sovereignty,
black box rule,
and normalised emergency.
The infrastructure is emerging; the emergency provisions are increasingly codified; the analytical tools to see it are now on the table.
References
Burstein, G. and C.V. Negoiță. “Foundations of a Postmodern Cybernetics Based on Kabbalah.” Kybernetes 40(9/10), 2011, pp. 1331–1353.
Burstein, G. and C.V. Negoiță. “A Kabbalah System Theory of Ontological and Knowledge Engineering for Knowledge Based Systems.” International Journal of Advanced Research in Artificial Intelligence 2(2), 2013, pp. 9–14.
Burstein, G., C.V. Negoiță and M. Kranz. “Postmodern Fuzzy System Theory: A Deconstruction Approach Based on Kabbalah.” Systems 2(4), 2014, pp. 590–605.
https://www.mdpi.com/2079-8954/2/4/590
Burstein, G., C.V. Negoiță and M. Kranz. “Kabbalah Logic and Semantic Foundations for a Postmodern Fuzzy Set and Fuzzy Logic Theory.” Applied Mathematics 5(9), 2014, pp. 1375–1385.
Burstein, G. “Foundations of a Postmodern Turn in Science, 2.0: A Kabbalah-Based Framework for Reconstructing Knowledge.” NOEMA XV(3), 2016, pp. 109–129
Burstein, G. and C.V. Negoiță. “A Kabbalah System Theory Modeling Framework for Knowledge Based Behavioral Economics and Finance.” In: Modeling and Simulation of Complex Social Systems (conference/collected volume), c. 2014–2015.
Appendix A: Glossary
Holon
An entity that is both a whole (with its own control loop) and a part of a larger whole. Each holon runs the same KST architecture at its own scale.Holarchy
A nested hierarchy of holons. Vertical links are:Parent Netzach → Child Keter (commands)
Child Malkuth → Parent Hod (outcomes)
Sefira (pl. Sefirot)
In Kabbalah: an emanation/attribute.
In KST: a functional control position (standards, identity, accreditation, data, audit, balance, outbound, inbound, actuation, settlement).Qliphah (pl. Qliphoth)
In Kabbalah: the ‘husks’ or shadow aspects of the sefirot.
In this paper: the inverted/emergency-mode form of each function (standards → decree, observation → total surveillance, constraint → automated punishment).Kabbalah System Theory (KST)
Burstein & Negoița’s formalisation of the Tree of Life as a recursive hierarchical feedback system for ‘humanistic systems’, using category theory, fuzzy systems, and control theory.Viable System
A system that contains the necessary sensing, decision, and execution functions to maintain its own existence.Recursive / Fractal Architecture
A structure where the same control grammar (ChaBaD / ChaGaT / NHY) repeats at multiple scales: global → national → institutional → programmatic → transactional.Programmable Money
Digital currency or tokenised liabilities with embedded conditional logic (rules at Da’at / Gevurah / Yesod) enabling automated enforcement at transaction level.Conditional Sovereignty
A configuration where a parent holon’s gates (Gevurah, Yesod) determine a child holon’s actual room for maneuver, even when formal sovereignty is preserved.Black Box Model
A decision system whose inputs and outputs are visible but whose internal logic is opaque (proprietary, classified, or too complex), enabling Satariel-type concealment at the Da’at layer.State of Exception
A legal-political condition where normal rules are suspended; in this framework, the trigger for qliphothic inversion of the architecture.
Appendix B: Implementation Sketch (KST Holon)
This sketch shows how the described control loop can be implemented as code. It is illustrative, not production-ready.
from dataclasses import dataclass
from typing import Dict, Any, List, Optional
from enum import Enum
from abc import ABC, abstractmethod
class SystemMode(Enum):
NORMAL = “tree_of_life”
EMERGENCY = “qliphothic”
@dataclass
class Command:
objectives: Dict[str, Any] # What to achieve
constraints: Dict[str, Any] # Boundaries and rules
budget: float # Available resources
trace_id: str # For provenance
mode: SystemMode = SystemMode.NORMAL
@dataclass
class Outcome:
metrics: Dict[str, float] # Measured results
settlement: Dict[str, Any] # Actual material state
provenance: List[str] # Execution path
trace_id: str
success: bool
violations: Optional[List[str]] = None
class Holon(ABC):
“”“
Abstract recursive KST holon.
Each concrete implementation wires Keter..Malkuth
to domain-specific logic.
“”“
def __init__(self, name: str, children: Optional[List[”Holon”]] = None):
self.name = name
self.children = children or []
self.mode = SystemMode.NORMAL
def run_frame(self, parent_cmd: Command) -> Outcome:
# Mode selection (normal vs emergency)
if parent_cmd.mode == SystemMode.EMERGENCY:
self.mode = SystemMode.EMERGENCY
return self._run_emergency_frame(parent_cmd)
# === COGNITIVE LAYER (Keter + ChaBaD) ===
policy = self.keter_refine(parent_cmd)
identities = self.chochmah_identify(policy)
institutions = self.binah_accredit(policy, identities)
model = self.daat_synthesise(policy, identities, institutions)
# === EMOTIONAL LAYER (ChaGaT) ===
telemetry = self.chesed_observe()
violations = self.gevurah_check(telemetry, policy)
if violations.get(”critical”):
return Outcome(
metrics={},
settlement={},
provenance=[self.name],
trace_id=parent_cmd.trace_id,
success=False,
violations=violations.get(”list”, [])
)
plan = self.tiferet_optimise(model, telemetry, policy)
# === ACTION LAYER (NHY) ===
child_cmds = self.netzach_commands(plan)
child_outcomes = self._collect_child_outcomes(child_cmds)
self.hod_validate(child_outcomes)
execution = self.yesod_actuate(plan, child_outcomes)
outcome = self.malkuth_settle(execution, parent_cmd.trace_id)
return outcome
# --- Normal-mode abstract methods ---
@abstractmethod
def keter_refine(self, parent_cmd: Command) -> Dict[str, Any]:
pass
@abstractmethod
def chochmah_identify(self, policy: Dict[str, Any]) -> List[Any]:
pass
@abstractmethod
def binah_accredit(
self, policy: Dict[str, Any], identities: List[Any]
) -> Dict[str, Any]:
pass
@abstractmethod
def daat_synthesise(
self,
policy: Dict[str, Any],
identities: List[Any],
institutions: Dict[str, Any],
) -> Dict[str, Any]:
pass
@abstractmethod
def chesed_observe(self) -> Dict[str, Any]:
pass
@abstractmethod
def gevurah_check(
self, telemetry: Dict[str, Any], policy: Dict[str, Any]
) -> Dict[str, Any]:
pass
@abstractmethod
def tiferet_optimise(
self,
model: Dict[str, Any],
telemetry: Dict[str, Any],
policy: Dict[str, Any],
) -> Dict[str, Any]:
pass
@abstractmethod
def netzach_commands(self, plan: Dict[str, Any]) -> Dict[str, Command]:
pass
def _collect_child_outcomes(
self, child_cmds: Dict[str, Command]
) -> List[Outcome]:
outcomes = []
for child in self.children:
cmd = child_cmds.get(child.name)
if cmd:
outcomes.append(child.run_frame(cmd))
return outcomes
@abstractmethod
def hod_validate(self, child_outcomes: List[Outcome]) -> None:
pass
@abstractmethod
def yesod_actuate(
self, plan: Dict[str, Any], child_outcomes: List[Outcome]
) -> Dict[str, Any]:
pass
@abstractmethod
def malkuth_settle(
self, execution: Dict[str, Any], trace_id: str
) -> Outcome:
pass
# --- Emergency (qliphothic) mode sketch ---
def _run_emergency_frame(self, parent_cmd: Command) -> Outcome:
“”“
Illustrative inversion: bypass deliberation,
intensify surveillance, automate sanctions.
“”“
# Thaumiel: concentrated emergency authority
# Satariel: opaque models
# Gamchicoth/Golachab: total monitoring + harsh enforcement
# Gamaliel/Nehemoth: record outcomes, but feedback legitimises more power
# Domain-specific implementations would plug into:
# - emergency_policy()
# - opaque_model()
# - mass_surveillance()
# - automated_sanctions()
# For brevity, we just return a failure outcome.
return Outcome(
metrics={”emergency_mode”: 1.0},
settlement={”mode”: “qliphothic”},
provenance=[f”{self.name}:emergency”],
trace_id=parent_cmd.trace_id,
success=False,
violations=[”emergency_inversion_active”],
)









Nested, recursive feedback-control fractal systems are self-contained.
No thinking-outside-the-box is possible.
Sorry, it does not appear Divine, but a corrupted algorithmic demiurgic shadow, so I'll have to dissent.
No offense, you understand. ;-)
American presidents have expanded and every year renewed government powers and procedures under a state of emergency declared in the days after 9/11.
The United States, at least, has not functioned since then as the Constitution might lead citizens to expect. Because various aspects of the emergency system remain state secrets, Americans cannot know precisely what their government is doing.
We do know, however, that agents of the US government, nearly all unelected bureaucrats, declared some Americans domestic violent extremists, DVEs.
The Tree of Life is a model, appropriated from kabbalah, used to enable and to clarify communication about a complex, partly covert system of governance and control.
If governance is even partly covert, i.e., resistant to FOIA requests even by senior legislators, at what point does the entire system become qliphothic, therefore, unconstitutional?