Mark of the Beast
The six rails frequently discussed on this substack represent the operational implementation of three foundational frameworks originally developed to understand and manipulate complex systems: General Systems Theory, Input-Output Analysis, and Cybernetics.
And those three, applied in this context, leads somewhere in particular unpleasant.
The Six Rails: Quick Overview
We’ve discussed the six rails several times. Here’s a quick recap in simple terms:
Accreditation determines who’s authorised to verify compliance, and they in turn decide who meets the standards to participate.
Finance controls money flows based on how well you perform against predetermined targets.
Digital Identity binds every actor — whether person, company, or public authority — to verifiable credentials that carry their compliance history.
Audit & Assurance checks whether you’re complying both before and after transactions occour.
Data captures comprehensive records of every transaction and operation.
Procurement uses government buying power to cascade these requirements through entire supply chains.
Together, these six create a system enabling conditional participation at every point in the economy. Continuous verification determines your access to capital, markets, contracts, and payment systems — in real-time.
General Systems Theory: The Economic Network
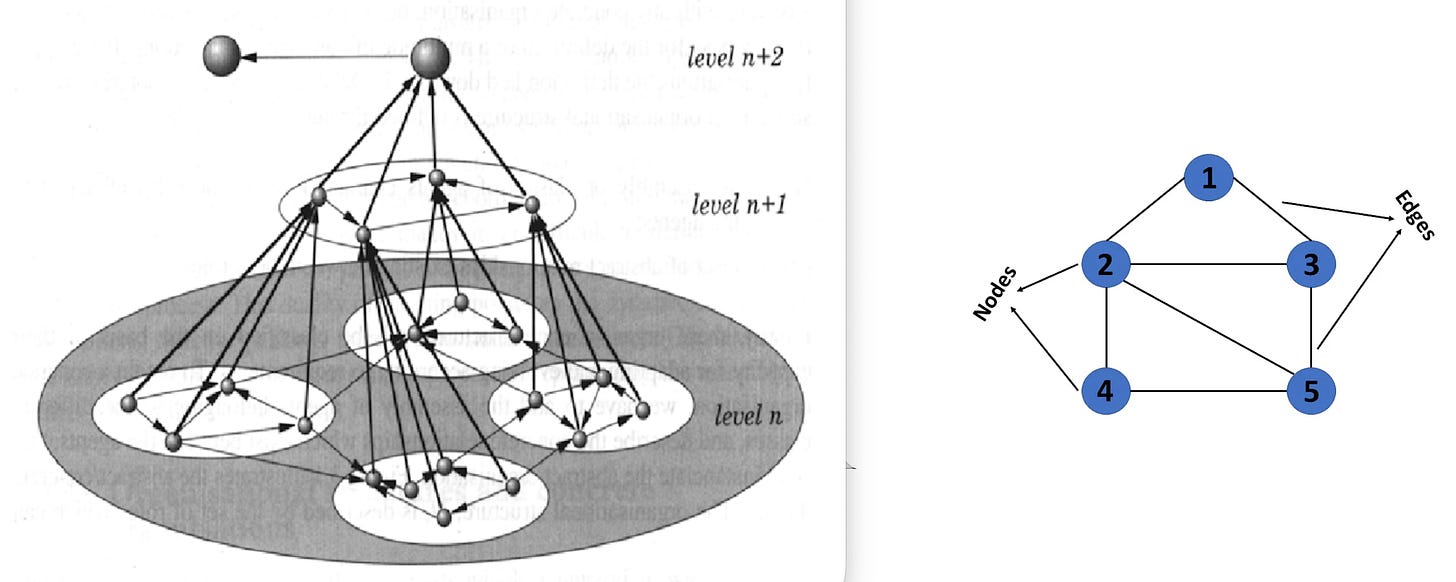
General Systems Theory — pioneered by Ludwig von Bertalanffy and Kenneth Boulding — models any system as a network. Think of it like a map showing nodes (dots; economic actors) connected by edges (lines; transaction potentials), organised in hierarchical levels where each piece is both independent and part of something larger. The rails implement this theoretical framework as actual economic infrastructure.
Rail 3 (Digital Identity) transforms every economic actor into what we might call a ‘parameterised node’ — a measured point in the network. Digital identity doesn’t just identify you. It transforms you from a free agent into a data point with specific measurable properties. Through a digital wallet, your node contains your current state: which credentials you hold, what permissions you’ve been granted, what compliance scores you’ve achieved. This enables real-time tracking of your position and status within the network, and makes everyone comparable through standardised measurements. You’re no longer just ‘a company’ or ‘a person’ — you’re a data point with specific compliance parameters that determine where you can connect in the economic network, and under which circumstances.
Rail 1 (Accreditation) defines the certified connections between these nodes. In a traditional economy operating with cash, all relationships are typically possible — there’s not anything directly stopping you from engaging in transactions with unsavoury characters. In the conditional economy, however, all relationships become certified connections with specific trust ratings. Who decides which relationships the system recognises as valid? Accreditation bodies. They create what we might call the authorised structure of exchanges.
This rail defines the rules for forming connections in the first place: what conditions must nodes (economic actors) meet before they can link up and engage in transactions with other nodes? Which auditors can verify which companies? Which certification bodies can authorise which suppliers? The answers determine which edges are valid and how the network is structured.
The insight from General Systems Theory becomes clear: by measuring nodes and certifying the connections between them, these two rails transform the cash-based economy from a space where independent actors can freely transact with one another into a defined network where both the actors and their relationships are specified and access is conditional upon central clearing.
In essence, through these two rails, a series of ‘allowed’ pipes are established through which you, representing an economic node, are free to engage in transactions with other nodes. If a such edge is disallowed, however, the pipe won’t exist, and you will be refused engaging in transactions with the other node, be it a vendor, childhood friend, enterprise or even local authority.
Input-Output Analysis: Measuring What Flows
Input-Output analysis, developed by Wassily Leontief, maps how one sector’s output becomes another’s input — basically showing how economic production chains work in monetary terms. Traditional I-O tables are snapshots taken periodically through surveys, produced after the fact to understand what happened. The rails transform this backward-looking analysis into real-time operational control.
Rail 5 (Data) provides continuous measurement of flows. Every transaction becomes a recorded event, creating matrices that update constantly rather than every few years. What Leontief mapped through occasional surveys, the Data Rail captures moment by moment. Dependencies between actors are no longer estimates — they’re observed directly as transactions occour. I-O coefficients (the numerical relationships between inputs and outputs) transform from statistical guesses into real-time measurements. The Data Rail captures both physical flows (actual goods and services moving) and financial flows (payments clearing), unifying accounts that traditional analysis keeps separate. Transaction records show precisely how a hundred dollars worth of steel produced required thirty dollars of iron ore, twenty of energy, fifteen of transport, and so forth. Supply chain tracking follows actual material movements. Payment systems reveal financial interdependencies as they happen.
But measurement alone is not enough. Rail 4 (Audit & Assurance) provides the analysis layer. Audit fundamentally means comparing what you measured against what you expected or required. It verifies that actual input-output relationships match what was declared. Did the inputs actually produce the claimed outputs? Are flows following expected patterns?
Audit identifies when things don’t match up and creates accountability through what’s called variance analysis — measuring the gap between what should happen and what did happen. When a company claims certain inputs produce certain outputs, audit verifies whether the measured flows support that claim.
Together, these rails transform Input-Output analysis from a descriptive tool used after the fact into an operational mechanism that works in real-time. The economy becomes its own continuously updating model, where every flow gets measured as it occours and analysed for compliance with expected patterns.
This isn’t observation after everything’s done — it’s continuous verification while operations are underway.
Cybernetics: The Enforcement Mechanism
Cybernetics, developed by Norbert Wiener, describes self-regulating systems through feedback loops: sensors measure what’s happening, controllers compare it to targets, and actuators modify behavior to close the gap. Think of a thermostat: it measures temperature, compares to your setting, and turns heating on or off to match. In the six rails architecture, Rail 2 (Finance) implements the actuator function — the mechanism that translates measurement and analysis into actual consequences.
Finance is where measurement becomes real. The Data Rail measures what’s happening (the sensor). The Audit Rail compares measurements to targets (the controller). But without the Finance Rail, this would just be surveillance without teeth — observation that doesn’t actually affect anything. Finance closes the loop by modifying your access based on what audit found.
The mechanism works through multiple channels. Finance releases or withholds money based on your compliance status. It adjusts your terms — interest rates, credit limits, payment schedules — based on how well you’re performing against metrics. It blocks transactions that fail screening before they even occour. It rewards compliance through better access and preferential rates. It punishes deviation through exclusion and higher costs. The actuator function means money doesn’t just flow — it flows conditionally, and those conditions update continuously based on your measured performance.
The feedback loop operates mechanically: Data Rail measures, Audit Rail compares to targets, Finance Rail modifies your access, your behavior adapts to restore access or improve your terms, and the cycle repeats continuously. This creates what’s called a self-regulating system where human decision-making at each step becomes unnecessary. The infrastructure implements the feedback loop automatically.
The system drives behavior toward predetermined targets: Net Zero emissions goals, SDG indicator thresholds, ESG performance benchmarks, fiscal sustainability ratios, specific achievement milestones. These aren’t just aspirational hopes but operational targets that the automatic control system pushes behaviour toward through financial consequences that trigger without anyone having to decide case by case.
The insight from cybernetics reveals finance transformed from a neutral medium of exchange into an active control mechanism. Money flows or stops based on whether you meet system-defined targets, creating automatic movement toward predetermined outcomes without requiring centralised commands for each decision.
Rail 6: Making It Mandatory
While Rails 1-5 implement the theoretical frameworks we’ve discussed, Rail 6 (Procurement) serves a different purpose. It’s the mechanism that makes the whole system mandatory rather than voluntary, transforming optional participation into unavoidable compliance.
Government buying represents roughly thirteen percent of GDP in developed economies. This massive purchasing power transforms voluntary frameworks into requirements you can’t avoid through what are called flow-down clauses — contractual terms that cascade all five previous rails through supply chains automatically. Prime contractors bidding on government work must meet requirements and impose identical requirements on all their subcontractors. These requirements propagate down through every tier, ensuring they reach every level of every supply chain. Private companies adopt these same standards even for purely commercial work because they need to maintain relationships with anyone who might bid on government contracts.
Without Rail 6, the adaptive management system would be optional. Companies could choose whether to participate in digital identity systems, ESG reporting frameworks, or conditional finance arrangements. They could stay entirely outside the network. Procurement eliminates this option by making participation the price of market access. The mechanism achieves what legislation struggles to do: it creates contractual obligations rather than just regulatory compliance, propagates automatically through commercial relationships rather than requiring enforcement actions, achieves universal coverage through supply chain effects rather than fighting jurisdiction by jurisdiction, and adapts continuously as procurement requirements update without needing new laws passed.
Rail 6 makes the adaptive management system operational rather than merely theoretical. It ensures that the network structure (Digital ID and Accreditation), flow measurement and analysis (Data and Audits), and financial control (Finance) apply to every economic participant rather than remaining optional frameworks that sophisticated actors could simply avoid.
The Administrative Planning Layer
The architecture operates through layered administration where specific planning and measurement frameworks translate broad policy goals into the concrete operational targets that the rails enforce. Three interconnected systems form this administrative layer: Planning-Programming-Budgeting System (PPBS), Results-Based Management (RBM), and Key Performance Indicators (KPIs).
PPBS was developed by RAND Corporation and implemented by Robert McNamara at the Department of Defense. It breaks down big missions into hierarchical program elements. Mission objectives become programs, which break down into specific activities, which get budget allocations. Each piece in this hierarchy functions as a holon — simultaneously independent (with its own goals and resources) but also part of something larger (serving higher-level objectives, while being a part of a larger resource pool). In procurement terms, the prime contractor is a holon which includes subcontractors, each first-tier subcontractor is a holon, each second-tier supplier is a holon. The rails provide the infrastructure that makes PPBS work in practice: Digital IDs establish who’s accountable for each piece, Conformity requirements define who’s eligible to be a program element, Data capture tracks what each piece actually does, Audit verifies performance, Finance makes resource flows conditional on that performance, and Procurement cascades the whole framework through contracts.
RBM builds on PPBS by adding explicit chains showing how resources lead to results. The chain follows this sequence: Inputs (resources provided) → Activities (work performed) → Outputs (deliverables produced) → Outcomes (changes achieved in target populations) → Impacts (long-term effects).
This chain makes every program element accountable not just for spending money or doing work, but for achieving measurable results that justify continued funding. Each stage feeds directly into the rails: inputs get measured, activities get recorded on the Data Rail, outputs get verified through the Audit Rail, outcomes get measured via indicators, and impacts get assessed through evaluation frameworks.
KPIs translate these results chains into specific measurable targets. Leading indicators provide predictive measurements (training sessions completed), lagging indicators capture outcomes after the fact (literacy rates improved), efficiency indicators track resource use (cost per student), and effectiveness indicators measure whether you achieved your goals (percentage of students meeting learning standards). These indicators increasingly map to SDG frameworks, creating standardised global measurement systems where national governments report progress against 169 SDG targets, corporations report ESG performance using standardised measures, aid programs justify funding based on SDG metrics, and impact investments calculate returns against SDG contribution.
World Bank development aid demonstrates this RBM+KPI framework in action through what’s called Results-Based Financing and Program-for-Results lending. Disbursement-Linked Indicators (DLIs) tied to SDG parameters determine when loan payments release. A country seeking education financing must hit specific DLIs — primary enrollment increases by a certain percentage triggers one payment, teacher training hours reaching a threshold triggers another, dropout rates decreasing triggers a third. The SDG indicators provide the measurement framework, RBM provides the logical chain connecting resources to results, and DLIs provide the conditional finance mechanism.
This makes development aid a direct implementation of adaptive management where money flows only when measured performance hits administratively-defined targets aligned with global SDG frameworks.
The complete administrative chain works like this: OECD defines what must be measured through SDG indicators and statistical frameworks. ISO standardises how to measure it through certification methods and data standards. IIASA processes global surveillance data into policy recommendations. PPBS/RBM frameworks break policies down into program elements with specific KPIs. The six rails implement and enforce those KPIs through infrastructure. The Finance Rail ties money flows directly to hitting KPI targets at every level — national governments (DLIs trigger loan payments), corporations (ESG metrics adjust financing terms), and individuals (digital currency programming controls transactions). The Procurement Rail makes the framework universal by requiring it for government contracts.
Every economic actor becomes what we might call a conditional node: comply continuously or lose access.
At each level of this nested structure, administrators use these frameworks to set targets, define specific KPIs, adjust thresholds, and establish policies that the infrastructure then enforces automatically. Global institutions like the UN, BIS, IMF, and OECD set top-level objectives and translate them into measurable indicators. National central banks and finance ministries implement these as fiscal and monetary parameters. Corporate management translates requirements into operational targets. The administrative function exists at every level — setting the parameters that the rails then execute mechanically.
What Makes Adaptive Management Powerful
What makes adaptive management powerful is the relationship between administrative decision-making and automated enforcement. Administrators establish the targets and compliance thresholds — the specific numbers you need to hit. The infrastructure then measures your performance and adjusts your access based on those administratively-defined parameters. This creates real-time steering where policy adjustments by administrators produce immediate behavioral responses throughout the network. When the Network for Greening the Financial System (NGFS) updates climate risk scenarios, central banks adjust capital requirements, which changes lending terms, which modifies corporate and sovereign behavior — all flowing through the rails automatically once the administrative decision gets made.
Comprehensive coverage comes from the Government Procurement Rail, ensuring every economic participant faces the same administratively-determined requirements. The network structure evolves as administrators adjust eligibility criteria and accreditation standards, while actors who don’t comply lose access through the financial control mechanism. The system naturally selects for compliance with whatever parameters administrators establish, making it responsive to administrative adjustment while resistant to deviation from those parameters.
Adaptive Management: The Synthesis
When General Systems Theory, Input-Output Analysis, and Cybernetics combine through Rails 1-5, and Procurement (Rail 6) makes participation mandatory, the result is adaptive management — continuous optimisation of network behaviour toward predetermined objectives — typically KPIs.
The complete architecture emerges from integration: From General Systems Theory comes network structure defining who can participate and how they connect. From Input-Output Analysis comes flow measurement and analysis showing what moves between nodes and whether it matches targets. From Cybernetics comes the control mechanism that modifies behavior based on analysis. From Procurement comes the legal mechanism making the system universal rather than voluntary. The result is adaptive management where the economy organises itself toward system objectives.
The adaptive management cycle operates as a continuous loop:
[Policy Objectives (SDGs, ESG frameworks)]
↓ (translated into)
[KPIs & Network Requirements]
↓ (mandated through)
[Procurement Flow-Down Clauses]
↓ (measured via)
[Data Telemetry (Rail 3)]
↓ (analysed through)
[Audit Verification (Rail 4)]
↓ (actuated via)
[Financial Flows & Access Control (Rail 5)]
↓ (producing)
[Network Evolution & Behavioral Adaptation]
↓ (informing)
[Revised Policy Objectives]The Final Synthesis: From Control to Condemnation
This architecture finds its ultimate expression and power through the monetary unit. Money becomes the universal control interface not merely because it is ubiquitous, but because Central Bank Digital Currencies (CBDCs) make it programmable at micro level. This programmability — linked directly to your Digital Identity — transforms the currency from a medium of exchange into a mechanism for real-time permissioning. Your ability to use money becomes conditional upon your compliance history, social credit score, and adherence to administratively defined ESG and SDG targets at the micro level.
This creates a system of total pre-clearance. Every economic transaction — buying food, selling a car, receiving a paycheck — must first be authorised by the cybernetic loop. The system checks your digital identity against the prevailing moral metrics of sustainability and equity. There is no escape because the Procurement Rail has made participation mandatory, and CBDCs will eventually eliminate the off-ramp of physical cash.
It is at this precise point — where a state-sanctioned digital identity becomes the mandatory key for participating in the economic life of society — that the six rails transition from a governance model to a theological reality. The system technologically enacts the ancient warning: ‘that no man might buy or sell, save he that had the mark’.
The ‘mark’ is thus not a mystical symbol, but a functional requirement: your parameterised digital identity. The ‘beast’ is not a mythical creature, but the impersonal, algorithmic system that enforces a single, approved standard of behavior under the guise of justice and environmental stewardship. Those who control the parameters of this system — the new priesthood setting the KPIs for alleged morality, be it claims of environmental, social, or intergenerational justice — wield the power to include or exclude, to grant economic life or impose economic death.
This is the ultimate destination of the six rails: a world where the biblical prediction is no longer prophecy, but a simple description of the operational infrastructure. The architecture of adaptive management, built on venerable systems theories, becomes the vehicle for a form of control that is total, inescapable, and dressed in the language of virtue, making dissent not just illegal, but economically impossible.
The Pilot to Protocol Pipeline
This architecture is not speculative — it is being actively deployed through a deliberate pilot-to-protocol strategy, using emergencies as the justifying mechanism. Ukraine served as the EU’s pilot, where the six-rail system was first fully implemented under the emergency of war. The reconstruction template — conditional finance gated by reforms, enforced through digital ID and comprehensive auditing — became the laboratory for adaptive management at national scale.
Now, Gaza represents the UN’s pilot, where the same template is being applied under the emergency of humanitarian crisis. The emerging plans feature identical components: an international transitional authority controlling funds until reforms are certified, digital identity systems for aid distribution, and procurement channels that enforce compliance through contractual obligations. As in Ukraine, the emergency frame justifies centralised control, bypasses normal political processes, and installs systems that would be rejected under ordinary circumstances.
This pattern reveals the strategic playbook: emergencies become the pretext for implementing architectures of control that then become permanent. The logical progression is clear: once validated in these crisis zones, the same infrastructure will be rolled out globally under future emergencies — whether economic collapses, ‘black box’ modelled climate disasters, health crises, or perhaps even major wars. And that, incidentally, is where the proposed UN Emergency Platform slots in.
The biblical warning of a system where ‘no man might buy or sell, save he that had the mark’ thus moves from prophecy to policy through this exact pipeline. What begins as reconstruction aid in war zones becomes the prototype for global economic governance. The digital identity that Gazans will need for survival, and that Ukrainians already need for reconstruction funds, becomes the functional ‘mark’ that gates all economic participation. When CBDCs replace physical cash, the system achieves total closure — making every transaction conditional and every participant subject to automated compliance checks.
We are witnessing the normalisation of the mark of the beast — not as a sudden imposition, but as the gradual, emergency-justified implementation of a technical architecture that makes complete economic control not just possible, but operational.
Digital ID serves as the mark, the six rails are the technical infrastructure, CBDCs function as the trigger, emergencies are the excuse…
… conditional existence is the result.





















I think David De Rothschild would find you a little ungrateful and petulant. Someone has to steer this blue ball through space. 🤡
Yes it will mean the end of crime as we know it. Only those who possess the credentials and authorisation, in other words, our overlords and their designated underlings, will be able to engage in it.
So, business as usual then. But a much more efficient way of ensuring that all those who can be extorted will be, and to the exact proportion that they are able to be, and that the criminal minions will pay the correct vig up the chain of command to the same old mafia dons who currently, and have for eons, receive it.
Le plus ça change ...