Asymmetric Recursion
Whether you examine ancient traditions, revolutionary political movements, modern corporations, or academic institutions, the same architectural pattern emerges again and again. And they all operate through a subtle yet powerful division.
This isn't about the content of these systems — whether spiritual, political, or scientific — but about their structure. The same grammar of control appears whether the text is the Kabbalistic Tree of Life, Marx's Communist Manifesto, Masonic degrees, Chile’s Project Cybersyn, Jantsch’s systems theory, contemporary Artificial Intelligence — or even an ESG compliance manual.
Ladders You Can Climb
Think of ‘Asymmetric Recursion‘ this way: you're allowed to climb a ladder as you wish, but you're not permitted to modify the ladder or even question where it leads. You can become an expert at ascending, even teach others how to climb — but the ladder's design and destination remain entirely beyond your influence.
This creates a peculiar situation. You feel empowered — you're learning, growing, participating, having real impact within the system. But you operate inside what amounts to an elaborate simulation of agency. You do have some level of freedom, but it’s within predetermined boundaries that you cannot examine or change.
The Participation Trap
Before examining specific systems, we need to distinguish between different types of involvement. Most institutions offer what one could consider procedural participation — you're invited to meetings, asked for input, given platforms to speak. This creates an impression of inclusion.
But procedural participation is entirely different from epistemic influence (where your insights can inform institutional decisions) — or moral influence (your values can shape foundational purposes).
The genius of asymmetric recursion lies in maximising procedural participation while minimising epistemic and moral influence. You're extensively consulted but systematically unheard. You can speak but cannot change. You're in every room — except the one where purposes get set.
The Anatomy of Asymmetric Recursion
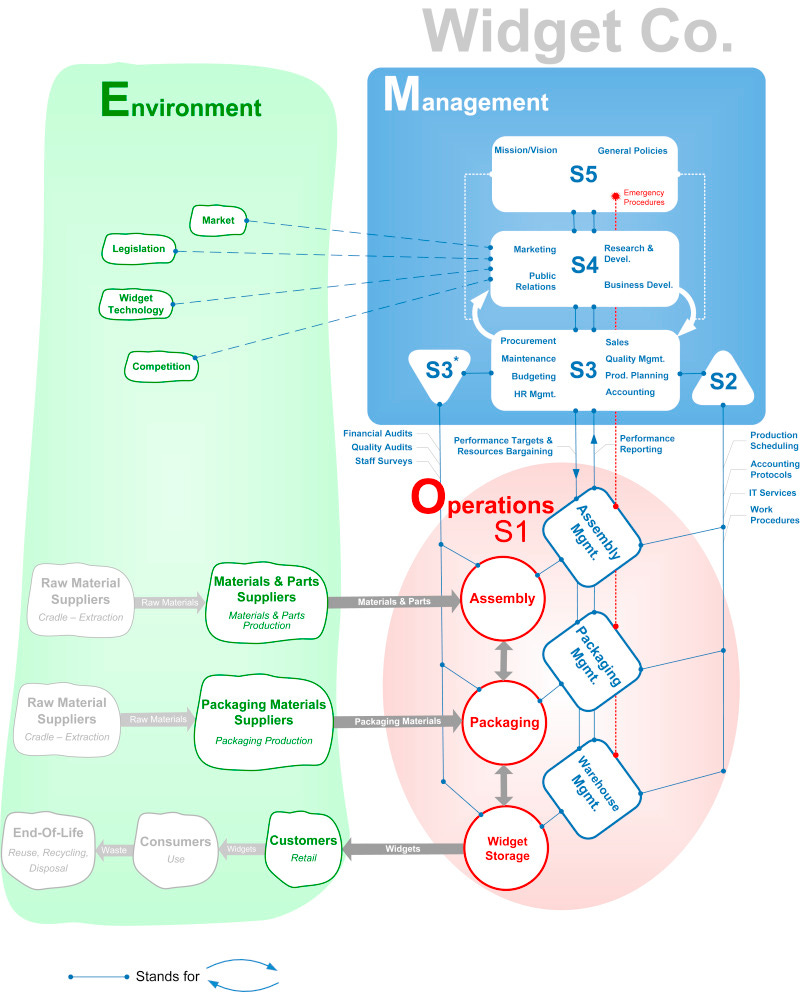
To understand how this works across such diverse systems, we need to examine the underlying architecture that makes it possible. The pattern operates through a consistent four-layer structure which resemble the Great Chain of Being1 — but which happen to map directly onto Stafford Beer's Viable System Model2:
L0 - Purposive (Beer's System 5)
Ultimate ends, identity, value weightsL1 - Normative (Beer's System 4)
Strategic principles, environmental adaptationL2 - Pragmatic (Beer's System 3)
Resource allocation, coordination, controlL3 - Empirical (Beer's Systems 2/1)
Operations, implementation, direct production
Beer's crucial insight was that viable systems require recursive feedback flowing both ways between all levels. Higher systems need information from lower ones to remain connected to reality; lower systems need direction from higher ones to maintain coherence. When this two-way flow breaks down, systems lose what Ross Ashby called ‘requisite variety’3 — they become unable to respond to the complexity of their environment. A situation which commonly leads to the collapse of the system.
Asymmetric recursion represents exactly this pathological state: write permissions flow only downward while upward influence gets systematically blocked. You get:
Extensive room to maneuvre at L3 (operations/tactics)
Some input at L2 (administrative processes)
Occasional influence at L1 (research and strategic principles)
No meaningful access to L0 (fundamental identity and purpose)
The system maintains operational dynamism while suffering from normative stasis. It can execute with great sophistication but cannot learn from its own consequences or adapt its fundamental assumptions. Beer would recognise this as a non-viable system — one that appears functional but has lost the recursive feedback loops essential for genuine adaptation4.
The trick lies in making L3 feel maximally participatory while keeping L0 maximally protected, creating what Beer might call ‘variety simulation’ — the appearance of systemic responsiveness without actual recursive capability.
Spiritual Software with Locked Code
The Kabbalistic Tree of Life5 demonstrates this four-layer architecture perfectly. At L3 (empirical), practitioners enjoy extensive read-write access: developing personal meditations, interpreting texts, experiencing mystical states. At L2 (pragmatic), there's significant participation in ritual coordination, study group organisation, and practical implementation of Kabbalistic principles.
L1 (normative) allows some theological interpretation within established frameworks — you can develop sophisticated commentary on divine attributes and mystical processes. But L0 (purposive) — the ten sephirot structure, the twenty-two paths, the fundamental cosmology of divine emanation and return to Ein Sof6 — remains completely sealed.
You can run any number of spiritual applications on this ‘divine operating system’, but you cannot revise the software. Kabbalah gives you ‘read-write access’ to practice and interpretation while maintaining ‘read-only permissions’ on the architecture itself. Questioning whether there might be eleven sephirot, or whether the Tree's hierarchical structure accurately maps reality, marks you as someone who doesn't understand the tradition rather than someone contributing to its evolution.
This is the Tree's grammar: participation in practice is unlimited; participation in design is forbidden. The containment mechanism is sacralisation — L0 assumptions become protected as divine revelation rather than human construction.
Institutional Mysticism with Locked Landmarks
Freemasonry provides another clear example of asymmetric recursion in mystical tradition, but with a more sophisticated deception than Kabbalah's openly protected cosmic structure. At L3 (empirical), Freemasons enjoy extensive participation in lodge activities, ritual performance, and fraternal interaction. At L2 (pragmatic), there's significant involvement in lodge governance, membership development, and administrative coordination.
L1 (normative) allows interpretation of Masonic symbols and adaptation of ceremonies within established bounds. But here Freemasonry reveals its architectural genius: rather than simply protecting L0 (purposive) through traditional authority, it sells the illusion of progressive access to L0 through the 33-degree system.
The degree progression from 1st to 33rd isn't arbitrary hierarchy — it's explicitly architected as a simulated journey toward divine transcendence, a travel from L3 to L2 to L1 to supposedly arrive at L0 access. Each advancement feels like progress toward ultimate knowledge and foundational authority, keeping members invested in climbing the ladder rather than questioning where it actually leads or why it exists.
Yet even the 33rd degree never delivers genuine L0 ‘write permissions’. The Ancient Landmarks7 — the three-degree system, the Hiram Abiff allegory8, the essential symbolic framework — remain immutable institutional DNA that no Masonic authority can alter, no matter how elevated their degree or how democratic the process.
The highest initiates still cannot rewrite the foundational allegories or fundamentally restructure the system's core assumptions. According to Morals and Dogma9, the 33rd degree is ‘he who balances the inequilibrium’ — but this grand cosmic role remains entirely within the predetermined framework. They've simply been given more elaborate stories about why these structures exist and perhaps more administrative authority within existing boundaries, told they're ‘cosmic balancers’ while remaining locked out of the actual mechanisms that create the imbalances they're supposedly empowered to address.
The containment mechanism isn't traditional authority but transcendence simulation — L0 structures remain protected by promising eventual access that never actually materialises, no matter how far you climb.
This reveals asymmetric recursion architecturally disguised as its opposite: systems that appear to offer a genuine path to foundational participation while actually perfecting the simulation of such access.
Developmental Lockdown
Ken Wilber's Integral Theory10 presents itself as a comprehensive map of consciousness and reality, but follows the same architectural pattern with an even more sophisticated transcendence simulation than Freemasonry. At L3 (empirical), practitioners can apply integral concepts extensively — mapping individuals and cultures, designing interventions, conducting research. At L2 (pragmatic), there's significant involvement in integral organisations, methodology development, and community building.
L1 (normative) allows interpretation of developmental principles and adaptation of integral frameworks to specific contexts. But here Integral Theory reveals its architectural sophistication: rather than simply protecting L0 (purposive) through academic authority, it sells the illusion of progressive developmental access to L0 through the levels of consciousness progression.
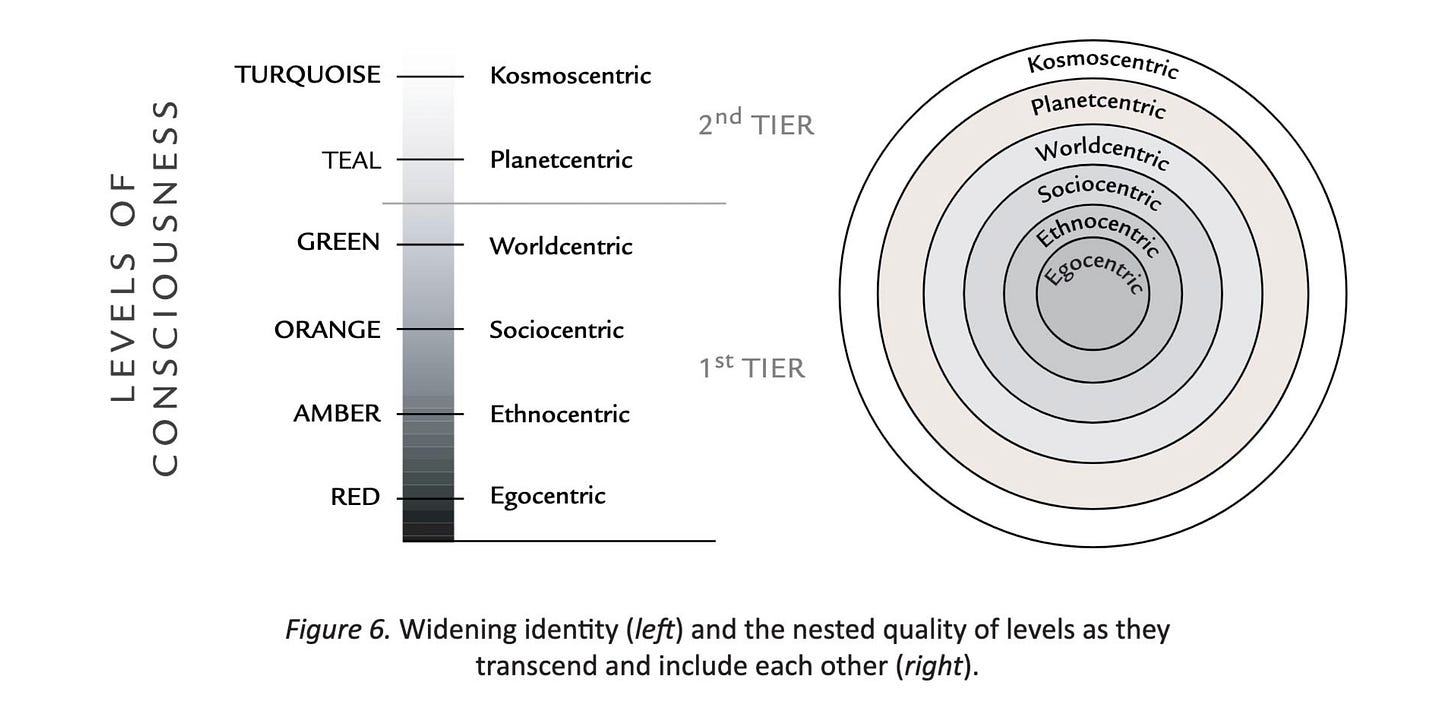
The developmental journey from beige (survival) through purple (tribal), red (power), blue (order), orange (achievement), green (community), yellow/teal (integral), turquoise (holistic), and beyond isn't arbitrary hierarchy — it's explicitly architected as a simulated journey toward ‘kosmic consciousness’11 and ultimate understanding. Each developmental stage feels like progress toward truth and greater capacity to perceive reality's fundamental structures, keeping practitioners invested in their own developmental climbing rather than questioning the ladder's design.
This transcendence simulation becomes even more sophisticated through associated frameworks like Don Beck's Spiral Dynamics12 and Marc Gafni's Unique Self13 theory. Beck's system promises that understanding ‘value memes’14 grants special insight into cultural evolution itself, while Gafni's framework positions practitioners as having transcended both ‘separate self’ and ‘no self’ traditions to reach the ultimate ‘post-postmodern’ spiritual stage. These extensions create elaborate self-justification mechanisms: practitioners feel they've not only reached higher developmental altitudes but have transcended all previous spiritual and psychological systems, making questioning the foundational framework feel almost regressive.
Yet even reaching the highest developmental altitudes — turquoise, coral, or beyond — never delivers genuine L0 ‘write permissions’. The fundamental assumptions about ‘kosmic’ evolution, the inevitability of developmental stages, the ‘transcend and include’ teleology, the AQAL framework itself — these remain sealed from revision no matter how ‘developed’ you become.
Try questioning the basic framework itself. Your critique doesn't get engaged on its merits; instead, it gets diagnosed as evidence of your developmental altitude. The system has evolved an immune response that converts criticism into confirmation of its own validity. Even the most ‘highly developed’ practitioners cannot fundamentally restructure the developmental hierarchy or question whether consciousness actually unfolds through predetermined stages.
The containment mechanism isn't altitude framing but developmental transcendence simulation — L0 structures remain protected by promising that sufficient personal development will eventually grant access to ultimate truth, while ensuring that even the highest stages remain locked out of the actual foundational assumptions that structure the entire system.
This reveals asymmetric recursion architecturally disguised as enlightenment: systems that appear to offer genuine developmental paths to foundational understanding while actually perfecting the simulation of such transcendence.
Personal transformation within these frameworks can be completely authentic — practitioners often experience meaningful shifts in consciousness, community, and spiritual growth. The system's ability to deliver real benefits at L3 while maintaining L0 control is precisely what makes asymmetric recursion so effective. The experience of elevation makes the structure of containment invisible. You're not climbing toward foundational access; you're climbing within foundational constraints that feel increasingly natural the higher you ascend.
Revolutionary Simulation and Systematic Transcendence
Marx and Engels’ Communist Manifesto appears to offer the opposite of mystical hierarchy — it promises workers control over their own conditions through revolutionary action. Yet it demonstrates identical architectural constraints. At L3 (empirical), workers get extensive tactical participation — striking, building solidarity. At L2 (pragmatic), there's involvement in party organisation, and resource coordination.
L1 (normative) allows some input on revolutionary principles, strategic planning and class analysis within established frameworks. But L0 (purposive) — historical materialism as scientific law, the inevitability of class struggle, the predetermined stages of economic development — remains protected as objective truth rather than theoretical choice.
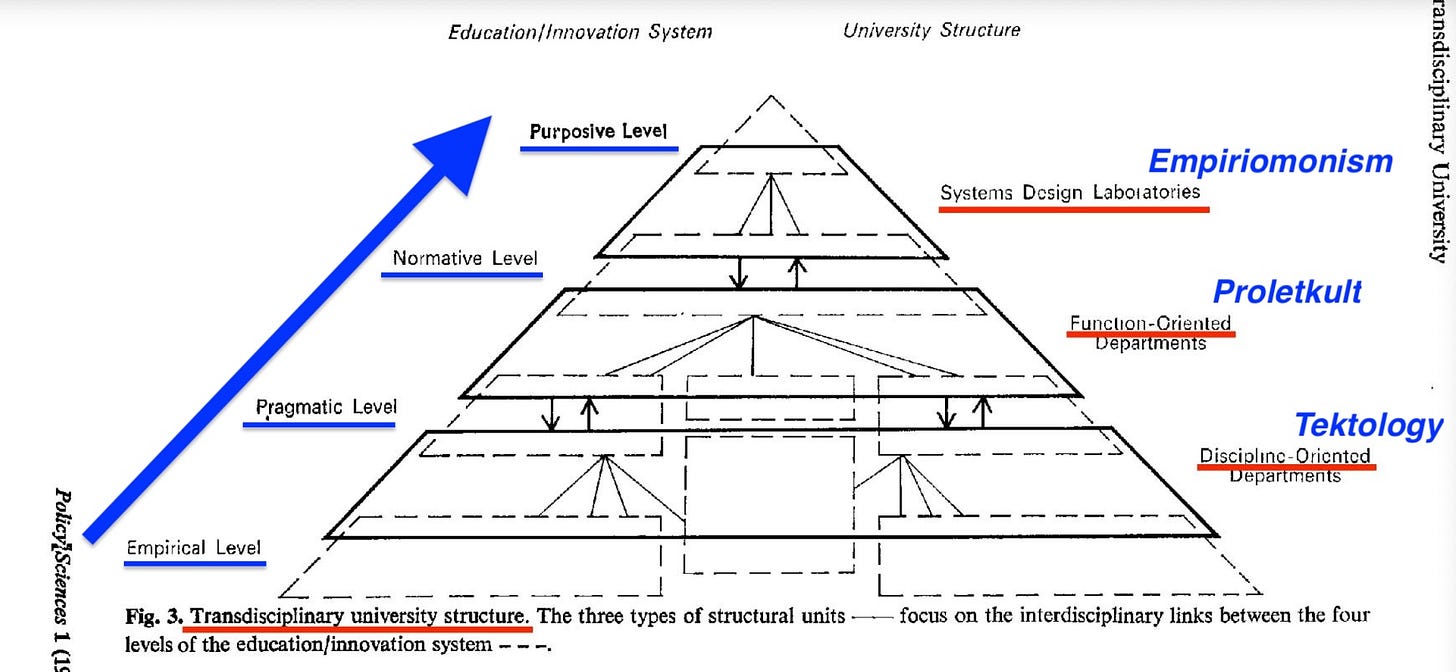
Alexander Bogdanov recognised this limitation and created a more complex transcendence simulation through his three-part system. His empiriomonism15 promised to translate knowledge at L0 (purposive) into information, proletkult16 would transform this at L1 (normative) into social energy, and tektology17 at L2 (pragmatic) would convert that into natural energy, finally reaching L3 (empirical) application. This appeared to offer genuine systematic transformation across all levels — a way for revolutionary consciousness to flow from foundational assumptions down through social organisation to material practice.
Yet Bogdanov's system maintained the same asymmetric recursion while making it architecturally invisible. Workers could participate extensively in cultural creation through proletkult and organisational design through tektology, feeling they were co-authoring the foundational knowledge structures through empiriomonism. But the systematic relationships between knowledge, social energy, and natural energy — the fundamental assumptions about how consciousness transforms material reality — remained sealed from revision by those experiencing the transformation.
The Manifesto creates the same division found in Kabbalah: extensive tactical participation combined with theoretical deference. You can participate fully in revolutionary practice while being excluded from revolutionary theory. Party intellectuals maintain ‘read-only’ control over the interpretation of ‘historical necessity’, whether framed through Marx's dialectical materialism or Bogdanov's early version of systems theory.
Contemporary ESG frameworks operate through identical logic. Stakeholders can provide input at L3 (operational metrics) and L2 (organisational coordination), but the fundamental assumptions — growth models, discount rates, burden-sharing formulas — remain technocratically managed at L1 and L0. The containment mechanism is scientific authority — L0 assumptions become protected as empirical fact rather than value choice.
Jantsch's University
Erich Jantsch developed the influential purposive-normative-pragmatic-empirical framework and applied it to university organisation18, explicitly recognising that viable systems require integration across all four layers: L0 purposive (ultimate educational mission), L1 normative (institutional principles), L2 pragmatic (administrative coordination), and L3 empirical (disciplinary research). This appears to create a pathway for genuine knowledge integration and institutional evolution through all levels.
In practice, it typically operates as asymmetric recursion. Faculty can participate extensively at L3 (knowledge production) and have some involvement at L2 (administrative coordination). They may influence L1 discussions about institutional principles and academic standards within established frameworks. But L0 — fundamental questions about the university's ultimate educational mission, its role in society, and institutional telos — remains controlled by administration and boards.
Modern universities exhibit this pattern consistently: faculty can innovate endlessly in their specialised domains while having little say in the fundamental educational mission their institution serves. The containment mechanism is administrative authority — L0 purposes become management prerogatives rather than scholarly questions subject to the same critical inquiry applied within disciplines.
Corporate Stakeholder Theater
Contemporary corporations have developed sophisticated stakeholder engagement that creates extensive L3 participation — employees influence workplace policies, customers shape product development, communities negotiate project implementation. L2 involvement includes input on administrative processes and operational coordination.
L1 sometimes allows stakeholder influence on principles like corporate social responsibility and governance standards. But L0 — fundamental corporate purposes, profit maximisation imperatives, shareholder primacy — remains beyond stakeholder reach.
ESG scoring systems exemplify this perfectly. Companies optimise across hundreds of L3 metrics while leaving L0 business models unexamined. The system encourages endless improvement within predetermined frameworks rather than questioning whether those frameworks align with public interest. The containment mechanism is fiduciary duty — L0 purposes become legal obligations rather than choices subject to stakeholder deliberation.
Technology Platforms: Digital Feudalism
Social media platforms offer extensive L3 participation — content creation, community building, application development. L2 involvement includes input on policy implementation and community governance. Platform governance initiatives occasionally allow L1 influence on content moderation principles and platform policies.
But L0 — algorithmic ranking, data collection models, fundamental business architectures — remains centrally controlled and largely opaque. Users can create endlessly within predetermined possibilities while having no influence over the systems that shape their digital experience. The containment mechanism is technical complexity — L0 decisions become expert domains rather than democratic choices.
The Universal Containment Mechanisms
Across these diverse systems, the same structural elements appear:
Impenetrable Firewalls
Core assumptions get protected by making them feel transcendent, scientific, or historically inevitable rather than constructed and revisable.Absorption Protocols
Criticism gets reframed as evidence of the critic's limitation rather than potential system insight. In mystical traditions, resistance becomes ‘ego’. In developmental frameworks, dissent becomes ‘lower stage thinking’. In political movements, questioning becomes ‘false consciousness’.Simulation Interfaces
Extensive participation opportunities create the feeling of agency while filtering out challenges to foundational assumptions. You can influence implementation while being excluded from purpose-setting.Linguistic Capture
Key terms get redefined so that dissent becomes difficult to express. Try arguing against ‘inclusive prosperity’, ‘spiritual evolution’, ‘saving the planet‘, or ‘science-based targets’ without sounding regressive.
Why This Pattern Emerges
This isn't necessarily the result of conscious manipulation. When any system needs coordination around shared assumptions, those assumptions naturally become protected from constant revision. The protection mechanisms then evolve increasingly sophisticated ways of maintaining legitimacy.
The Tree of Life, Communist Manifesto, Integral Theory, and corporate governance structures all face the same underlying challenge: how to enable participation while maintaining coherence — how to allow change while preserving meaning.
Asymmetric recursion represents one solution — but it’s a solution that sacrifices adaptability for a simulation of responsiveness. A solution which typically end up collapsing under its own weight, as reality moved on while bureaucrats were busy, competing to make it to the top of the hierarchy.
Asymmetric Recursion by Design
Asymmetric recursion often emerges organically in complex systems, but it can also be deliberately engineered into institutional architecture. Arthur Schlesinger's 1961 CIA restructuring proposal19 provides a significant example of conscious asymmetric recursion design. Under this framework, intelligence operations would be carried out by the CIA (L3), administrative coordination would flow through the Forty Committee (originally 303 Committee) at the State Department (L2), while research and strategic planning would be split between Robert Amory Jr's proposed surveillance division and the Council on Foreign Relations (L1).
This created a perfect asymmetric hierarchy: intelligence operatives could execute missions with tactical flexibility, but had zero access to the fundamental purposes and strategic logic driving those operations. The architecture ensured that those carrying out activities remained systematically isolated from those determining why such activities served broader institutional goals. Even strategic planners at L1 remained disconnected from the ultimate decision-makers who set foundational priorities at L0. JFK's resistance to this particular restructuring — and his dismissal of Amory followed by placing him under surveillance20 — suggests recognition that such architectures concentrate power while diffusing accountability, creating what Beer would call 'non-viable' governance systems that cannot learn from their own consequences.
This reveals the deeper stakes of recognising asymmetric recursion: it's not just an abstract pattern but the conscious architectural logic being embedded into our most powerful institutions.
The Symmetric Threat
The true stakes of asymmetric recursion become clear when we examine what happens to genuinely symmetric alternatives. Project Cybersyn in Chile represented exactly what Beer's Viable Systems Model prescribed — real-time economic coordination where operational feedback could actually reach policy levels, where workers had genuine input into economic planning, where the system could learn and adapt based on lived experience.
Cybersyn — in its limited trial — demonstrated that genuine L3→L0 feedback was not only theoretically possible but practically viable. Rather than simulating participation, it enabled actual recursive governance. Rather than protecting foundational assumptions from reality, it made economic policy responsive to operational consequences. For those implementing asymmetric recursion in global governance, this represented an existential threat — proof that their architectural choices were deliberate rather than inevitable.
The system had to be destroyed.
Two Systems
When you examine all these systems for genuine upward communication — whether people's actual experience can inform foundational decision-making within the existing framework — it becomes clear that out of everything we've analysed, only two systems actually allow information to flow from bottom to top.
Kabbalah is designed so that practitioners' spiritual work affects higher realms. The Tree of Life structure stays fixed, but your mystical experiences, devotions, and insights can influence divine purposes. The framework doesn't change, but information does flow upward through it through 11 paths.
Project Cybersyn enabled factory workers' operational data to directly inform national economic planning. The cybernetic theory remained constant, but real-time feedback from the shop floor continuously shaped policy decisions at the top.
Every other system? They block upward information flow entirely.
Freemasons can perform elaborate rituals, but their experiences never inform higher Masonic purposes — communication flows only downward through prescribed meanings. Integral practitioners can report developmental insights, but these get processed through predetermined altitude frameworks rather than informing the theory itself. Revolutionary activities confirm Marxist analysis rather than shaping it. University research rarely influences institutional mission. Corporate feedback optimises operations without reaching foundational business purposes. Social media engagement generates data that gets harvested, not heard.
This reveals something crucial: most systems that feel participatory are actually designed as information extraction mechanisms rather than genuine communication channels. You provide extensive input that gets processed for optimisation purposes — but it never quite reaches the level where foundational decisions get made.
The pattern shows that even allowing information to flow upward within existing frameworks is apparently threatening enough that most institutions avoid it entirely.
The Stakes
The pattern becomes problematic when systems lose the ability to hear their own consequences. When operational feedback cannot flow upward to inform foundational decision-making — even within existing frameworks — systems become increasingly divorced from the reality they're supposed to serve.
But the deeper problem is that most modern institutions don't simply ignore feedback — they simulate responsiveness. They create elaborate participatory interfaces that feel like genuine listening while technically blocking upward information flow. These aren't broken communication systems; they're sophisticated simulation systems designed to create the psychological experience of being heard while disallowing legitimate influence.
The simulation becomes visible when stakeholders who fail to agree with predetermined project directions get quietly ‘iterated’ out of the process. Suddenly their participation becomes ‘unconstructive’, their perspectives ‘misaligned’, their continued involvement ‘counterproductive to consensus-building’. Agreement, it turns out, was always more important than input. The system wanted participants, not participation; validation, not information.
This, ultimately, can best be described as ‘participatory theater’: it's not just ineffective communication, but legitimacy manufacturing. When people believe they're genuinely participating, they become invested stakeholders in systems… that actively exclude them from influence. The simulation prevents revolt by making containment feel like empowerment. Why question a system you feel you're co-creating?
This isn't about changing core assumptions or revolutionary transformation. It's about basic institutional responsiveness: can the people implementing policies inform the people setting them? Can operational experience reach strategic planning? Can those affected by decisions influence those making them? Or do systems only harvest agreeable information while cycling out sources of disagreement?
This analysis reveals that almost no major institutions allow even this minimal upward information flow. Instead, they've perfected participatory theater — extensive consultation processes, feedback mechanisms, and engagement platforms that generate the feeling of democratic input while ensuring operational reality never disturbs foundational decision-making.
Understanding asymmetric recursion reveals why so many promising movements — spiritual, political, academic, technological — end up reproducing the same deaf authority relations they initially seemed to replace. The problem isn't the content but the architecture: systems that simulate listening while systematically preventing hearing.
Project Cybersyn proved that genuine institutional responsiveness is not only possible but viable. That it was destroyed so quickly after the Chilean coup suggests that even basic listening — letting operational reality inform strategic decisions within existing frameworks — represents an existential threat to architectures designed around simulation rather than communication **.
The pattern is universal. Recognition is the first step toward distinguishing genuine responsiveness from its sophisticated simulation. True recursion isn't a ladder you climb, but a mirror that reflects the whole system back to itself — letting even the lowest rungs change the highest purpose.
** This is not to be taken as a recommendation of Salvador Allende’s regime, not marxism in general. Anyone reading this substack should be aware of my strong position on that particular ideology. This is simply addressing Project Cybersyn itself.